The slide deck containing all slides from the conferences.
Read more about fuzzing in my last blog post “Hack the Hacker – Fuzzing Mimikatz On Windows With WinAFL & Heatmaps (0day)”
Demos
Demo 1
CTF Challenge “Chat” (SECCON CTF – Try to find the vulnerabilities)
Demo 2
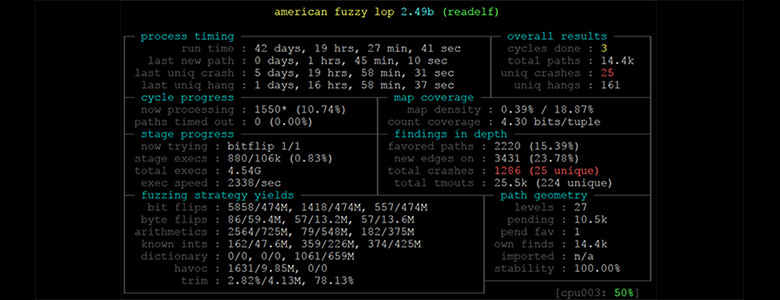
AFL Fuzzing workflow with FFMPEG as example
Demo 3
Short demonstration of LibFuzzer
Demo 4
Fuzzing Mimikatz with WinAFL and Taint Analysis
Demo 5
Using breakpoints to extract coverage information. Example with Adobe Reader.
Demo 6
Demonstration of DynamoRio DrCov to get coverage information from Adobe Reader.
Demo 7
How to detect when a PDF finished loading
Demo 8
Demonstration on finding the start and end address of the target function which should be fuzzed in-memory (Example with HashCalc).
Demo 9
In-memory fuzzing of HashCalc with WinAppDbg (750 exec / sec)
Demo 10
In-memory fuzzing of HashCalc with DynamoRio (170 000 exec / sec)
Demo 11
Fuzzing interactive applications with a self written fuzzer to discover deep bugs (which are not found per default by AFL)
Demo 12
Enabling GFlags and Application Verifier on Windows to identify vulnerabilities in mimikatz.
This research was done by René Freingruber (@ReneFreingruber) on behalf of SEC Consult Vulnerability Lab.