Fabian Densborn and Bernhard Gründling of the SEC Consult Vulnerability Lab recently discovered several security vulnerabilities in popular parental control apps for the Android platform. During their analysis, they found out that the parent web dashboards were susceptible to cross-site request forgery (CSRF) and cross-site scripting (XSS) attacks.
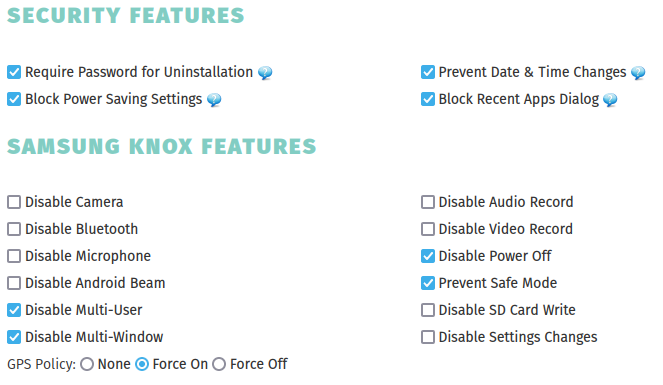
These vulnerabilities allowed the attacker to bypass the restrictions set by the parents, or even attack the parents themselves. Additionally, the Android apps’ restrictions imposed by the parents could be easily bypassed by the children by removing the necessary permissions in the settings app or by using the safe mode feature of Android. Since many of these apps collect a lot of private data of children, and some may even store the data in the cloud beyond the reach of GDPR, the privacy of the surveilled children may be at risk.
The SEC Consult Vulnerability Lab is already in contact with some of the vendors mentioned below through our responsible disclosure process. The identified security vulnerabilities should be fixed in the near future, according to the vendors. We are going to release further technical details through security advisories after those patches are publicly available.