It sounds like old news but cyberattacks are on the rise. Hordes of ransomware gangs paralyzed corporations worldwide in 2020 and demanded ransoms of sometimes several million USD, or hundreds of Bitcoins. Ransomware is easy to detect because its purpose is, after all, to be detected. Only through an easy-to-detect ransomnote attackers have a chance to get the ransom paid to their crypto wallets. Other types of cyberattacks are much more inconspicuous and thus more difficult to detect: Espionage attacks from Advanced Persistent Threats (APTs). Often, these are only discovered by chance by system administrators when attackers make a mistake after months of compromise or when a new security tool is rolled out that exposes the attack.
Top 5 Of The Simplest And Most Effective Measures To Prevent Hacker Attacks
defence
Attack Patterns
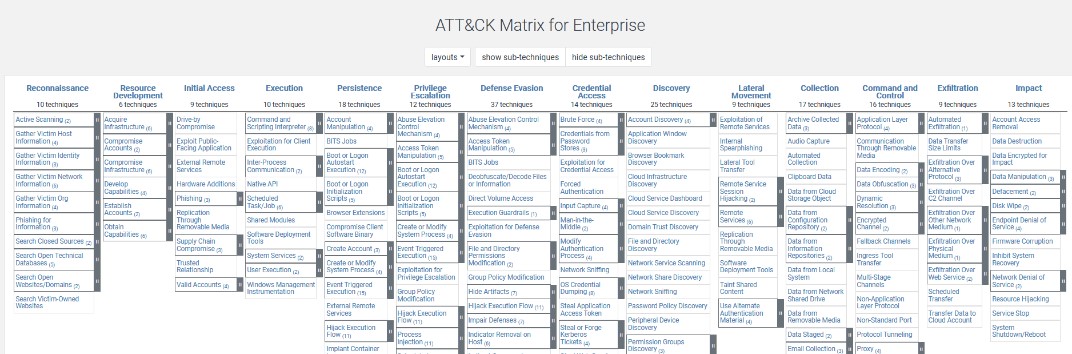
No matter what type of attacker you are dealing with, the steps from initial compromise to full domain domination follow the same patterns. Attackers rely on different techniques for different purposes and goals. For years, Mitre Corporation has provided a detailed collection of known techniques and tactics used by threat actors through the "Att&ck Matrix." It is designed to give enterprises and blue teamers an overview of hacking techniques and an understanding of how to protect yourself against them. Mitre Att&ck is supported by many security tools and used as a reference model by incident responders around the world.
Preventing attackers from using their standard repertoire of hacking tools gets them into big trouble and puts defenders in a much better position: many hackers are deterred and look for easier targets. In addition, the particularly persistent must dig deeper into their bag of tricks to reach their target, which significantly slows down the attack. These alternative activities can generate alerts in security products such as a security information and event management (SIEM) or endpoint protection that provide defense or detection. Time is critical in a security incident. There is a massive difference between identifying an attack within a day or a month. The sooner the attack is detected, the more likely it is that an attacker has not yet widely compromised the network and the damage can be contained.
Pareto Principle
Despite a wide variety of techniques and tactics used by hackers, a few basic measures can make it incredibly difficult for attackers to infect enterprise systems. But with just five security measures, loosely based on the Pareto principle, 80% of attacks can be successfully prevented with just 20% of the effort. And all that without spending tens of thousands of Euros on security products. If the following security concepts are consistently adhered to, an attack can often be nipped in the bud. Even if malware infects the system, it can hardly spread, cannot reload tools and cannot take over other users. Hackers would therefore have to dig deeper into their bag of tricks to completely hijack the company.
Top 5 Measures To Prevent Hacker Attacks
Tip No.1: Secure Permission Concept
The top priority is to secure administrative users of any kind. A general rule is: No administrator account is required for daily office work. Selected roles in defined departments therefore have a normal everyday user and an additional local administrator account that is not domain joined. If Windows requires elevated rights for an action (User Account Control - UAC), the credentials for the local administrator account are entered into the login screen so that the operation can continue. However, the user works exclusively with the non-admin account; this also applies to IT staff.
Also, the additional administrator users should not be assigned freely. The average user does not need access to administrator rights at all. Under no circumstances should passwords from administrator accounts be reused. Every user, especially privileged ones, needs their own strong password.
One wrong click is enough to infect the system with malware. The malware then "inherits" the permissions of the user account that activated it. Since management is a frequent target of attackers, no exception of this “no admin” rule should be made – especially for top management. By compromising a local administrator, it is usually possible to dump all stored passwords on the system (NTLM hashes, Kerberos tickets, tokens or even plain text passwords). If passwords are reused on other systems, attackers can trivially spread throughout the network.
From SEC Defence's point of view, the above-mentioned problem is the main reason for rapid compromise of corporate networks.
Other equally important recommendations:

Tip No.2: Application Whitelisting
Attackers like to use specialized hacking tools to read passwords or network movement. An initial downloader on the system downloads further malware to pursue further targets. Appropriate application whitelisting (only explicitly allowed applications can run) removes the possibility for attackers to run executables or scripts that are not explicitly allowed. Application whitelisting can be implemented in Windows through AppLocker or the newer variant Windows Defender Application Control (WDAC).
WDAC rules can be whitelisted based on signature, binary metadata, Microsoft reputation, path or parent process. WDAC only works on current Windows 10 versions as well as Windows Server 2016.
AppLocker has existed since Windows 7 and allows files to be executed based on signature, metadata in the binaries, or the respective path.
Professional hackers still find ways to circumvent application whitelisting. Using so-called "Living off the Land Binaries and Scripts" (or Lolbas), attackers abuse valid executables that Microsoft ships with and use them for their own purposes. A detailed compilation of Lolbas with their respective purposes is available on Github.

Tip No.3: Network Segmentation
Network segmentation means dividing the company's internal network into different logically and technically separated areas. The most commonly implemented segmentation is into an internal network and a demilitarized zone (DMZ). The DMZ hosts publicly accessible systems that are shielded from other networks by one or more firewalls. The background: if a system in the DMZ is infected, the attacker cannot spread throughout the entire internal network, but can at most take over the entire DMZ. This is like the concept of firebreaks in firefighting.
This concept should also be used within the internal network. There is usually no reason why an employee from the HR department should have access to the development server.
It’s best to restrict network traffic according to the "need to know" principle. If an attacker infects an HR notebook in such a case, for example, the infection can only spread further in the network with considerable effort. However, if the network is "flat," i.e., many employees have access to many areas, a single infection can affect the entire organization within a very short time.
Network segmentation can be achieved by dividing different departments or roles into corresponding VLANs with appropriate routing rules. Solid network segmentation is not something that can be implemented in an afternoon.
The importance of taking on this task as a company and implementing a secure network architecture cannot be overemphasized.

Tip No.4: OS And Application Patching
It should be common knowledge that software should always be kept up to date. Nevertheless, many attacks can be traced back to systems that have not been properly patched. Regularly published vulnerabilities in standard software lead to regular waves of attacks on these products.
Examples of this are SolarWinds Sunburst (even if it is an injected backdoor, the problem can be fixed by an update), the notorious SMB vulnerabilities EternalBlue or MS17-010 or also the vulnerability in Citrix Application Delivery Controller aka Shitrix.
New patches sometimes cause problems in systems, which is why people are often reluctant to install them early. Companies should first test published updates from manufacturers on a small scale before rolling them out across the board. Alternatively, companies can wait a month after a patch has been published, before installing it to see whether relevant media draw attention to possible "side effects". Apart from emergency patches, it’s not necessary to assume a massive problem if the patch is applied a month later. It is essential that a continuous and proper patch management process is established and lived in the company.
Don't be the company that has to explain to incident responders why Windows XP systems are still in productive use in the event of a breach.

Tip No.5: Asset And Lifecycle Management
"Should user xyz run Powershell commands on the system?"
If this question is answered with "We don't know the system", there is probably no proper asset management in place. It is too common for a victim of a cyberattack to not know which system on their network is for which purpose, which employees are responsible for it, or who should have access to it. It is incredibly difficult to detect abnormal behavior on a system when it is unknown what actual normal behavior looks like.
This refers not only to systems, but also to users or programs. In this case, we also speak of "Shadow IT", IT assets that operate on the network unnoticed by IT administrators. Shadow IT is a massive problem, especially for large corporations. Malware that has persisted on these systems is hardly ever found. How could it be, if even the existence of the system is unknown ...
Running assets should be tracked in an asset management tool with the current patch status, responsible person and use case, as well as other current information. Following this procedure, a responsible person who can answer all questions about the system, can be quickly identified. Systems that are no longer needed must be taken out of operation by the established lifecycle management to ensure that they won’t be used for testing purposes forever.
Preparation Is Key
There is no such thing as one hundred percent security. Even a well-prepared company can be hit by an attacker. But you minimize the likelihood of being hit and the impact after an attack is limited to a few assets. A few compromised systems can be quickly rebuilt, and a few passwords can be easily reset, allowing normal business operations to continue.