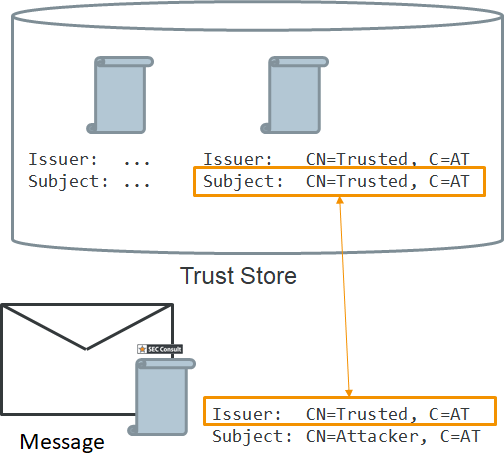
Last year SEC Consult demonstrated an attack against a software used for identifying German citizens online where anyone could assume an arbitrary identity. Now it was time to think a lot bigger and have a look at a similar software that is used all across the European Union.
In June SEC Consult had a look at eIDAS-Node. This is a software library that allows Member States to take part in the cross-border authentication scheme eIDAS. Each Member State has its own mechanism to authenticate its citizens – eIDAS interconnects these national eID schemes. For instance, this allows any EU/EEA citizen to use a national idenfication scheme to authenticate against a service in another Member State. SEC Consult again found a critical vulnerability that allowed an attacker to authenticate as the famous writer “Johann Wolfgang von Goethe” – or any living citizen.
My Name Is Johann Wolfgang Von Goethe – I’m Back To Prove It (Again)
eIDAS (electronic IDentification, Authentication and trust Services) is an EU regulation that (among other things) defines a way for citizens to authenticate using their national electronic identification scheme (eID) when accessing services from other member states. It is intended to allow citizens to file tax declarations, enroll in a university, open bank accounts, pay online etc.. Citizens can still use their existing national eID schemes – eIDAS provides the regulation and standards for attaching national eID schemes into the European eIDAS network.
The following blog post provides an overview about the critical security vulnerability. For further technical details and proof of concepts see our security advisory here.
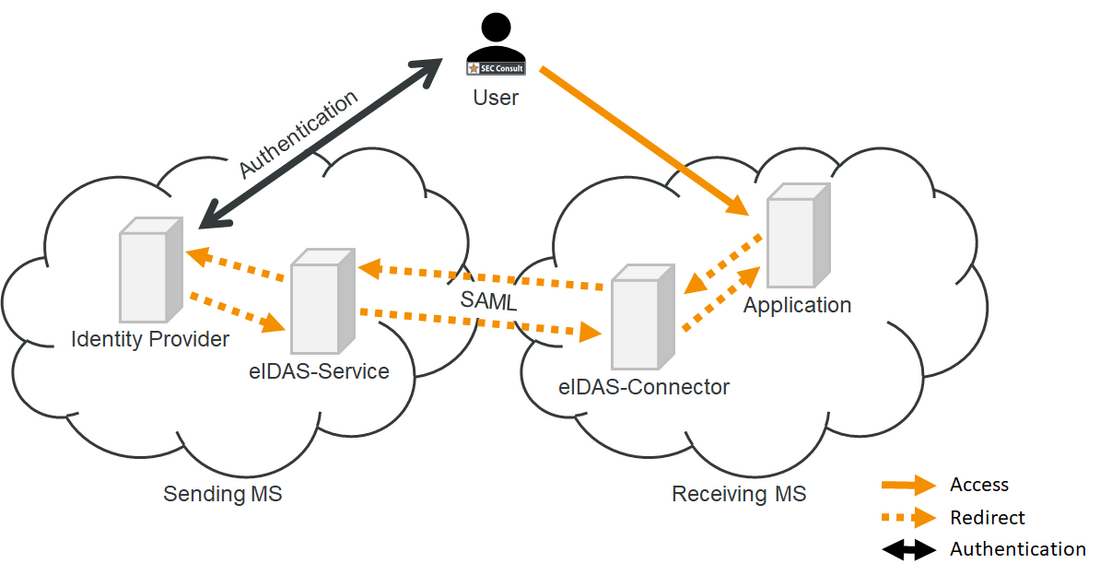
eIDAS overview
As an example, if an Italian citizen wants to authenticate against a German online service, first the German eIDAS-Node (eIDAS-Connector) is directed by the web application to initiate the authentication process. It sends a request to the Italian eIDAS-Node (eIDAS-Service). The Italian eIDAS-Node forwards the user to a system that is equipped to authenticate the Italian citizen using the national eID scheme. After authentication, the German eIDAS-Connector receives the citizen’s information which it forwards to the web application.