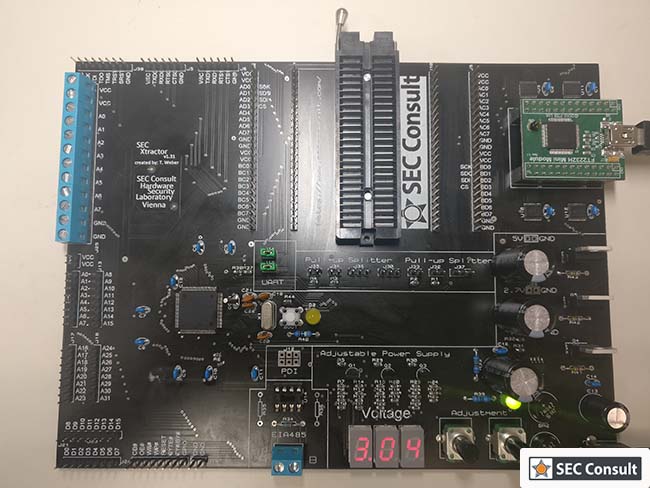
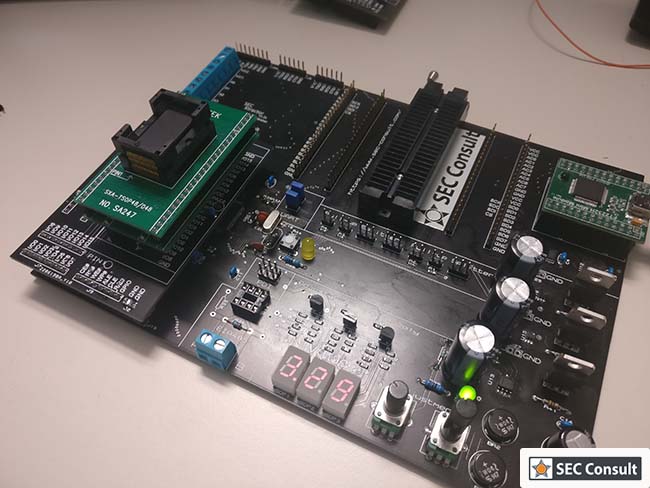
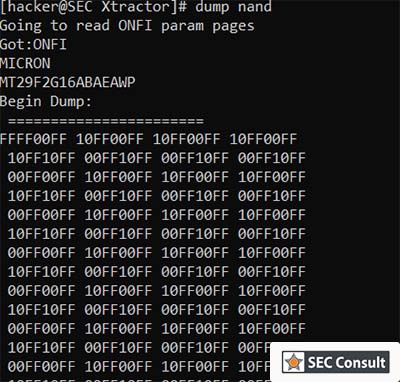
It comes with an easy to use and configurable memory reading concept that supports multiple ways to read flash chips (e.g. NAND chips). As its firmware and hardware are completely open-source, it can be easily extended. Interface identification is another requirement that was fulfilled by integrating JTAG brute-forcing and UART scanning. It can also be used as an OpenOCD adapter and it provides two UART-to-USB bridges. Most devices require anything between 1.8 and 5.5 volts, which is supported by the SEC Xtractor.
Motivation
During the very first holistic penetration tests of embedded devices (hardware and firmware), the SEC Consult Hardware Lab used a bunch of different tools with all pros and cons. Most of them, like the Flyswatter 2 or the Shikra, had some kind of UART-to-USB bridge or were able to directly interface with SPI and I2C.
A large number of them were based on the same chip series, developed by Future Technology Devices International Ltd., mostly the FT2232 or FT232. As it was easy to buy a breakout board for the big FT2232HQ chip online, it didn’t take long for a prototype to be developed.
In the end, as no other tool could fulfill all the requirements (especially the ability to read NAND and NOR interfaces) the decision was taken to design a new fitting tool. This resulted in the development of the SEC Xtractor.
EARLY DAYS IN THE HARDWARE LAB OF SEC CONSULT
Nearly ten years ago, SEC Consult already performed some hardware security assessments in the field of smart metering, ATM security and some routers/gateway devices. Later, SEC Consult conducted a study on the security of smart home devices already with hardware security in mind. In 2015, SEC Consult took the first steps to create a dedicated Hardware Lab for security research and hardware security assessments for customers. The first setup work was done by former colleagues Stefan Riegler and Christian Kudera. End of 2015, Thomas Weber ordered some serious equipment to perform in-depth penetration tests in this field of IT security. Basic and high-end equipment was shipped from different shops and the first in-depth projects were finally undertaken in the last quarter of 2015.
The first issues with hardware security assessments came under many aspects:
- How can we read this TSOP48 NAND flash memory?
- Does anyone have this special screw driver in the office?
- I killed the target device, do we have another one?
One of the biggest challenges was the varieties of embedded devices. They had different voltage levels, different flash memory types, different microcontrollers and so on. This led to the use of many different flash memory interfaces required to conduct a basic firmware audit.
SPI, NAND