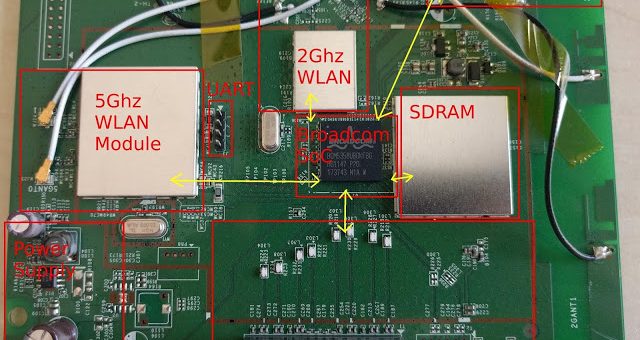
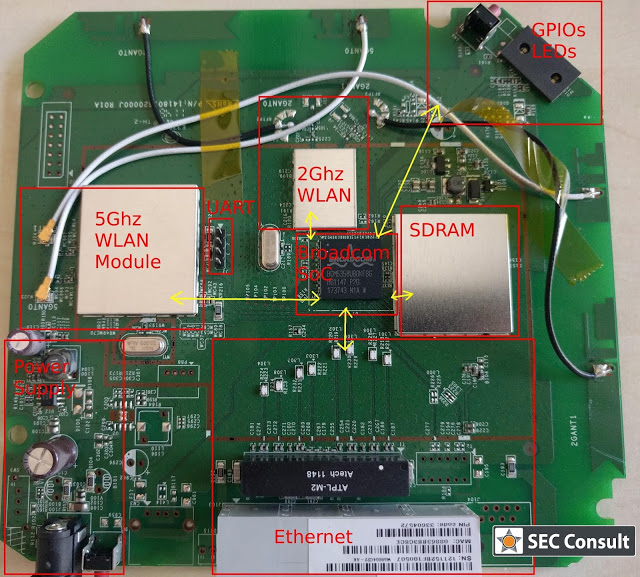
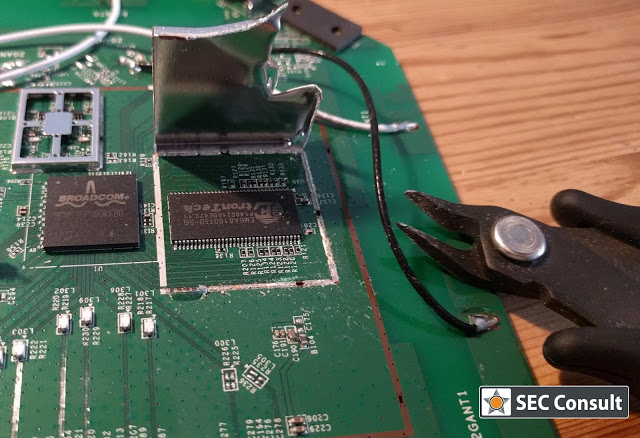
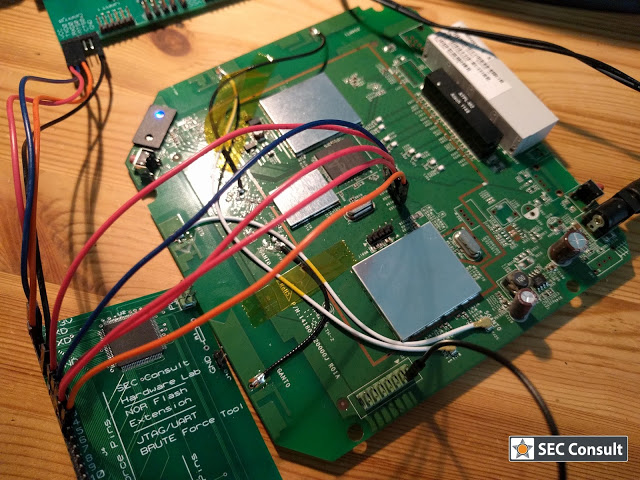
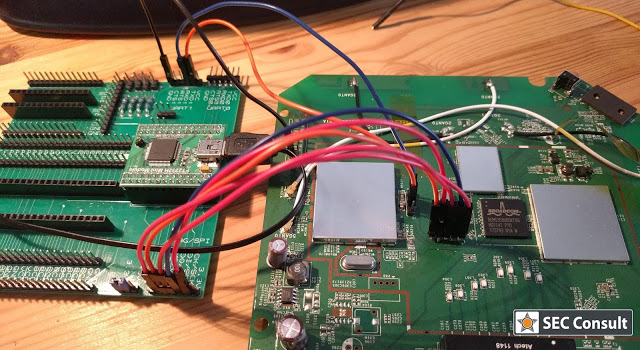
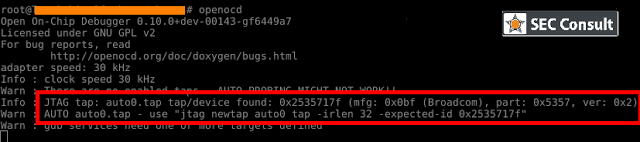
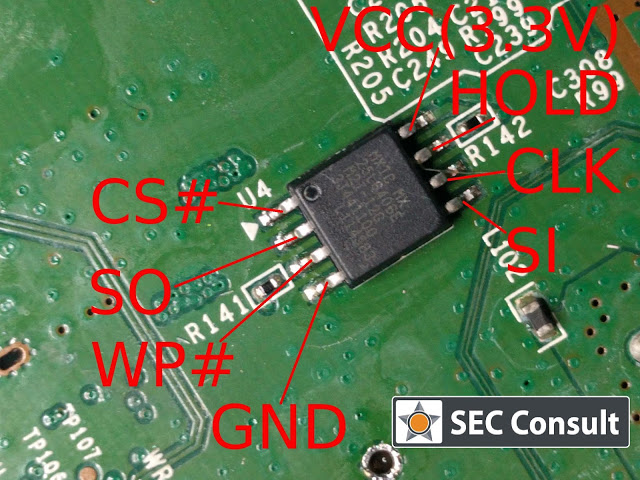
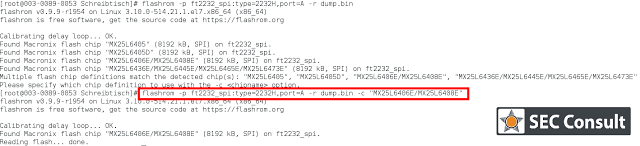
SEC Consult operates a dedicated Hardware Security Lab as part of its SEC Consult Vulnerability Lab. The presented material is a glimpse into ongoing research at the SEC Consult Hardware Security Lab and pentests that involve hardware hacking techniques.
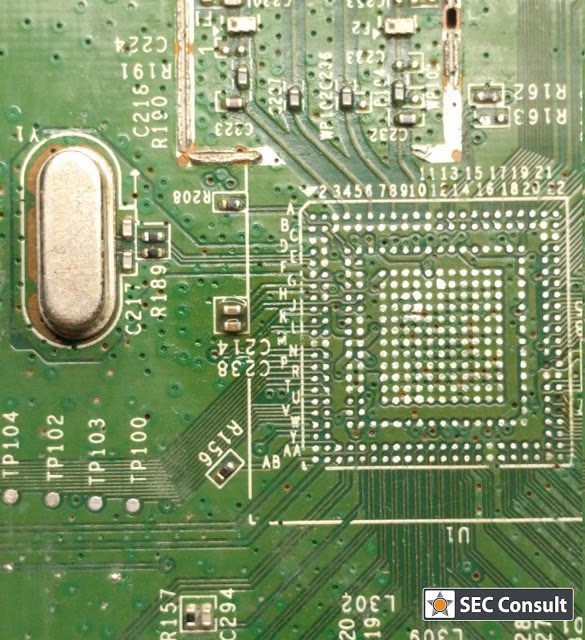
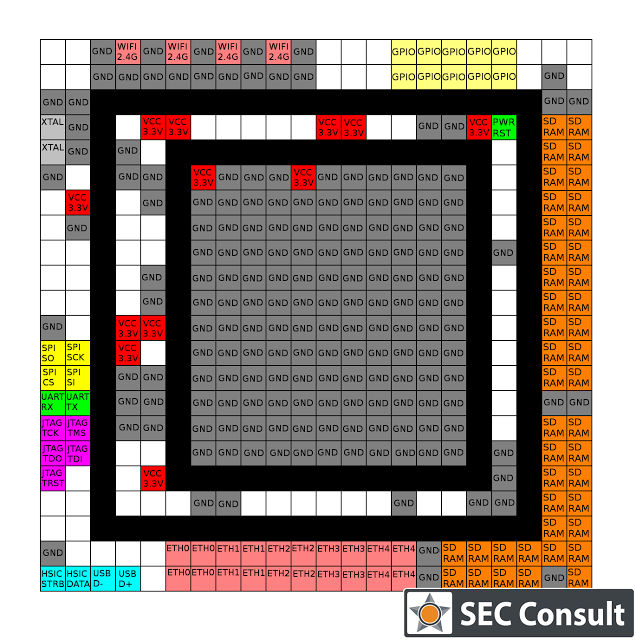
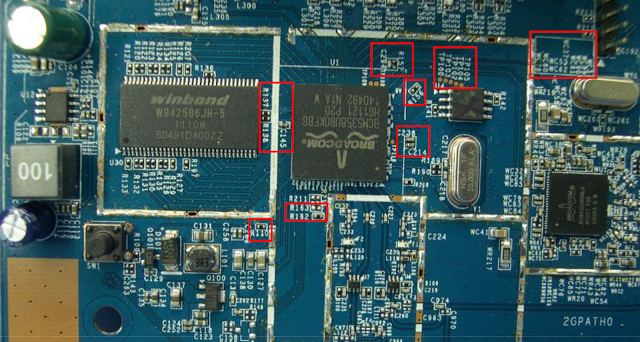
Nowadays, we are living in a world dominated by embedded systems. Everyone can be spied on through various channels. Routers, IP-cameras, phones, and other embedded devices are affected by security vulnerabilities and are therefore easily hack-able. Recent outbreaks of Mirai and other IoT-based malware reinforce this observation. To audit the firmware of such a device in-depth – either out of curiosity or for customers as part of increasingly mature security programs – we have to disassemble it and find debug interfaces. Only a debuggable and running system can reveal all of its secrets. This process is invasive and usually leads to damaged devices – hence, more than one device is mandatory for in-depth analysis!
How To Proceed With Known Devices
A quick workaround for avoiding a costly analysis of embedded devices are alternative firmwares. Large companies can easily run acceptance tests of a vendor-built firmware by security consultants to minimize dangers of such systems before they buy a bunch of IoT devices. But there are only few alternatives for users and hobbyists. They can install alternative firmware from third parties like OpenWRT. This firmware does not always have a better performance than the original one (because of the proprietary chip-sets) but it is often a more secure alternative.
When we are charged with a security audit of a stock firmware from a known device, the hardware analysis part is often reduced to a online search in some relevant forums (mostly the OpenWRT Wiki).