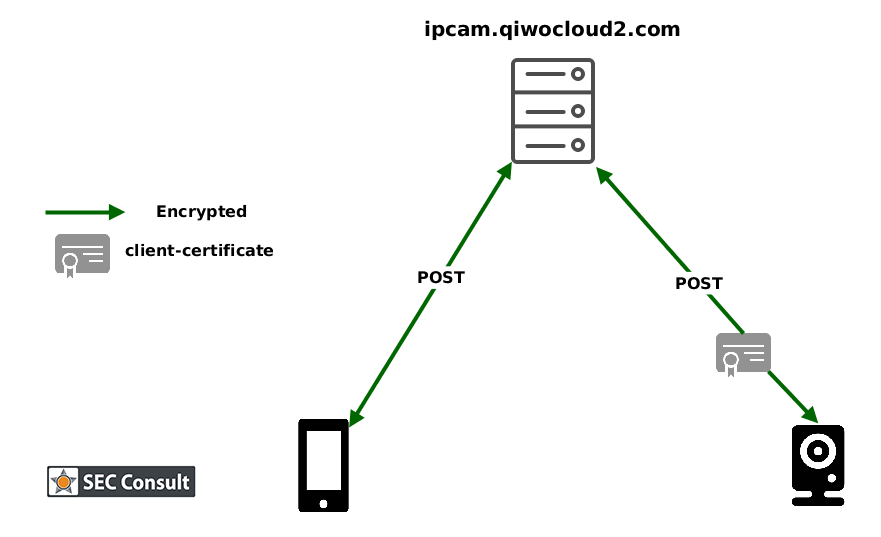
The analysis of observed HTTPS traffic between the baby monitor and the cloud service indicates the usage of a client SSL certificate authentication on the baby monitor.
Without supplying a valid client certificate, it is not possible to observe and intercept the HTTPS communication of the baby monitor. But by extracting the client SSL certificate (which is identical on every baby monitor world-wide!) and static private key enabled by an identified vulnerability, HTTPS traffic originating from the baby monitor can be observed and intercepted. Similar problems with static encryption keys/certificates used by multiple devices have been found by SEC Consult in the past in the House of Keys research and followup the review 9 months afterwards.
Extracted client certificate:
-----BEGIN CERTIFICATE-----
MIIDAzCCAmygAwIBAgIBDzANBgkqhkiG9w0BAQUFADBrMQswCQYDVQQGEwJjbjES
MBAGA1UECAwJZ3Vhbmdkb25nMREwDwYDVQQHDAhzaGVuemhlbjENMAsGA1UECgwE
cWl3bzENMAsGA1UECwwEc2RjcDEXMBUGA1UEAwwOcWl3b2Nsb3VkMS5jb20wHhcN
MTUwNTI1MDkzMzU4WhcNMzgwMTIwMDkzMzU4WjCB0TELMAkGA1UEBhMCQ04xEzAR
BgNVBAgMCkd1YW5nIERvbmcxEjAQBgNVBAcMCVNoZW4gWmhlbjETMBEGA1UECgwK
UUlXTyBHcm91cDENMAsGA1UECwwEUWl3bzERMA8GA1UEAwwIcWl3by5jb20xHDAa
BgkqhkiG9w0BCQEWDWNlcnRAcWl3by5jb20xRDBCBgkqhkiG9w0BCQIMNXsicHJv
ZHVjdFR5cGUiOiJxaXdvX2lwY2FtIiwiYmF0Y2hOdW1iZXIiOiIyMDE1MDUyNSJ9
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDW8KwHzU5aNgDQwXEmKBrXrEY/
TKbwK3r4XKUlH2eUM0UmVBpnHzz9JQy0WSNs28CSpQlqwOTrODw4QS7PJcXrpqgA
V2E85DSx4RG/NAwD0bZdBIUEUHJfuTmSQ+Hwn8gXivjPBXjQb1oJ9BNu+SGLx8p+
MQTbj6/YIkjKV1qcKQIDAQABo1AwTjAdBgNVHQ4EFgQUHaGks8jt/3onjRiasDwP
MJxzOTQwHwYDVR0jBBgwFoAUpnSBwb/95nsc7+xVvn76i82QYMMwDAYDVR0TBAUw
AwEB/zANBgkqhkiG9w0BAQUFAAOBgQBB8fPH2WoIVr75Ik4QWwK37ANClpapfKUe
oTjvWOehYjBB+AndkVi6yFPwUj54vwdO3XBxYaxsGwuK4UsF8XwYWCA5aprmQqka
LjJvJAeCdvEWRA0WNTg8yGD4l2i+OsUgmK4kxS5BWuPje18y3Cbq/DHqeQiwoKFj
1zGuTI6+Kg==
-----END CERTIFICATE-----
As one can see, the client certificate used for all Mi-Cam devices is valid for quite a long time and has been issued by Qiwo.
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=cn, ST=guangdong, L=shenzhen, O=qiwo, OU=sdcp, CN=qiwocloud1.com
Validity
Not Before: May 25 09:33:58 2015 GMT
Not After : Jan 20 09:33:58 2038 GMT
Subject: C=CN, ST=Guang Dong, L=Shen Zhen, O=QIWO Group, OU=Qiwo, CN=qiwo.com/emailAddress=cert@qiwo.com/unstructuredName={"productType":"qiwo_ipcam","batchNumber":"20150525"}
SHA1 Fingerprint= DF:E0:C0:30:B9:0D:7D:F1:43:F8:FB:EE:19:8A:08:3A:3E:11:41:25
SHA256 Fingerprint= 79:9F:92:BD:D2:DD:06:3F:B9:93:55:F5:ED:EA:DC:D4:E8:7D:70:AF:D0:A9:92:48:A5:D7:E4:98:F6:F6:F1:E1Kalay Platform
The observed network traffic indicated no common audio and video transmission protocols. Nevertheless, the usage of a proprietary protocol with obfuscated stream characteristics used for transmitting audio and video stream was identified. We were able to deobfuscate the network traffic between the Mi-Cam and the cloud and were able to automate decoding and extracting video feeds from captured traffic (pcap). We will publish further details in an own blog post on this topic in the future once the research is completed.
Further analysis of the firmware and network traffic of the video baby monitor pointed to an IoT ecosystem called "Kalay Platform". The Kalay Platform is an IoT cloud connection platform and operated as a product of the Taiwanese based company ThroughTek Co., Ltd and was already mentioned by Brian Krebs regarding other security vulnerabilities (Foscam) in 2016. At the time of writing this blog post, ThroughTek states on their website to have over 300 million monthly connections. Interesting to mention is also that ThroughTek received the ISO27001 certification in October 2017 which includes the Kalay platform.
Affiliation to QiWo and Qihoo 360
The analysis of the network communication and numerous additional information such as domain registrants, indicated the involvement of a third party which was not publicy described or advertised. The third party in question is the Shenzhen based company Shenzhen QiWo Smartlink Technology Co., Ltd. which advertises a range of internet connected devices at their website qiwo.mobi including a camera designed for monitoring children. Various leads discovered during the analysis of the Mi-Cam and the fact that both qiwo.mobi and misafes.com only differentiate in domain name and used language but feature almost identical products, indicated a connection between both vendors. Further research has shown that the wording MISAFES is a registered trademark (serial number: 86621737) in several categories and currently owned by the entity SHENZHEN QIWO SMARTLINK TECHNOLOGY COMPANY LIMITED. This leads to the assumption that miSafes is a subsidiary company of Shenzhen QiWo Smartlink Technology Co., Ltd., with the purpose of sales and distribution of its products in the western market.
Shenzhen QiWo Smartlink Technology Co., Ltd. is according to its CEO Fengko Gao, a joint venture with the Shenzhen based large internet security company Qihoo 360 Technology Co. Ltd., which is well-known for their antivirus and browser products.
Beside miSafes several other vendors (such as Qihoo 360) sell the same or a very similar looking version of the video baby monitor on the amazon.com website. The following images display the variety of products, that have not been reviewed (yet) but based on the affiliation it stands to reason that the identified security issues also affect those other vendors.
Vulnerabilities
The following vulnerabilities describe issues of the Android application & cloud service and the video baby monitor and its hardware. During our investigation the main focus was to analyse the communication between the app, the video baby monitor and the cloud infrastructures but not the applications (Android, iOS) themselves.
- Authentication Bypass
- Missing Password Change Verification Code Invalidation
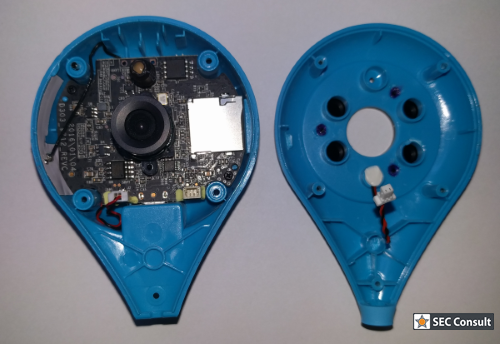
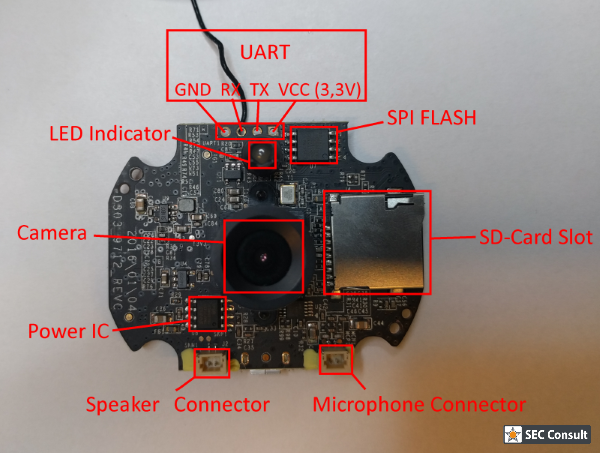
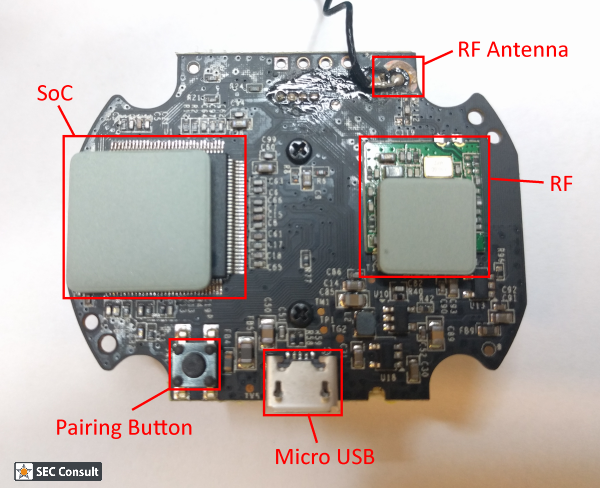
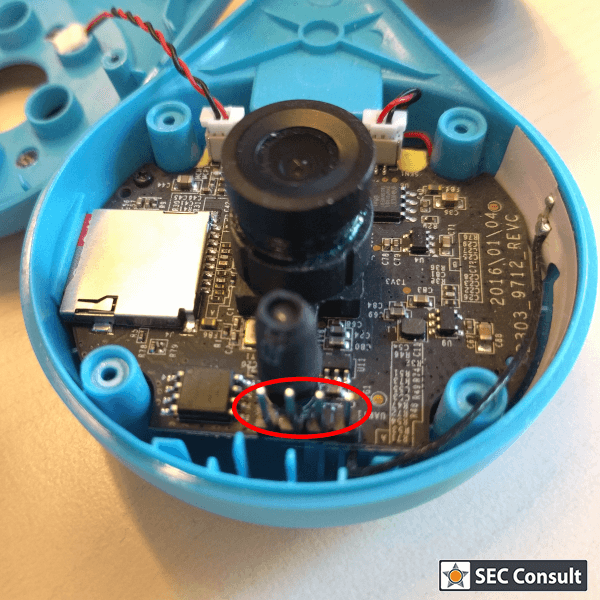
- Available Serial Interface
- Weak Default Credentials
- Enumeration of user accounts
- Outdated and Vulnerable Software
SEC Consult is following a responsible disclosure approach and since no fix for the discovered vulnerabilities is available, no material containing detailed information about the vulnerabilities will be released to the public.
Further information on the issues can also be found in our technical advisory.