Busting The Bad – When Criminals Scam The Wrong Company
vulnerability

The digitized and networked world is a richly stocked supermarket with countless bargains and special offers for hackers. Project plans, patents, designs, and customer data are out there, almost as if they were waiting for a motivated cybercriminal to pull out a few tricks.
Each year, far too many companies fall victim to fraud, blackmail, espionage, phishing emails, DDoS and man-in-the-middle attacks, part of which might have been prevented if IT security was taken seriously. Are you aware of the risks?
Let’s do a quick test. Imagine your company will be hacked and sensitive information about products, processes, customer data and other internal documents will fall into the wrong hands. Could it lead…
- to a loss of your business basis, because protected processes or formulas are leaked?
- to a loss of trust in your company (and people turn their backs on you)?
- to a threat to your employees?
- to criminal charges due to a violation of privacy laws (like the GDPR)?
- to a loss of sales due to an interruption of business?
[multiple-choice]
If you answered Yes more than once, keep on reading.

With A Great Network Comes Great Responsibility
Deception is a cyber-security approach that does not rely on simple threat hunting. Quite the opposite.
Firewalls, anti-virus programs or intrusion-detection systems are often the only defense barrier around IT structures in enterprises. Unfortunately, even if these systems are kept up to date (and they must be constantly updated and maintained to be of any help), they can be undermined easily.
Rest assured: absolute security is an illusion. Any unknown and unpublished software vulnerability can and will be exploited by professional attackers at some point, allowing them to access even well guarded systems through an unsecured back door. And then there’s the human factor. Phishing attacks are (annoyingly) still the most common and efficient way to infect IT infrastructures. Moreover, many employees don’t even know that cyber criminals have already infiltrated their corporate network or how inconspicuously this could happen on a daily basis. According to recent studies and the experience of our SEC Defence team, cybercriminals are often inside corporate IT systems for at least 100 days or more before they are discovered. This is a huge problem.
But don’t worry, we have your back! We’ve assembled 5 tips and tricks to sharpen your perception of potential attack vectors. You can easily implement them in everyday life.
Busted #1 (Aka: I know this guy)
People are biased whether they admit it or not. They read what they want to read and not necessarily what is actually written. You’ll also find an endless amount of studies out there, confirming the fact that the human brain has a neat trick to correct words with spelling errors and cybercriminals take advantage of this auto-correction feature, e.g. when faking e-mail addresses or the like.
TIP: Pay attention to your gut feeling and don‘t open any e-mails that already seem weird. If in doubt, don’t be shy to contact your IT guy and ask for his professional opinion (that’s what he is here for after all). If needed, he can implement filters to minimize the amount of scams you get via your corporate mail servers. To verify an unknown person from an otherwise legit company domain, simply press “reply” (without actually sending the message) or use the option to “show all headers” in your e-mail client to verify the sender’s actual mailing address.

Busted #2 (Aka: I need this, like, right now)
These things usually happen at the end of a long workday, the very moment you want to pack your things and go home. You check your e-mails one last time and receive a message from your boss, asking you to make a last minute wire transfer. Of course, all of this is strictly confidential. The recipient of the mentioned bank transfer is no stranger, but obviously a new partner in that law firm which has represented your company for many years. The amount to be transferred is not alarming, since a similar purchase was done last quarter. And of course, your boss is not available and must not be disturbed at his monthly meeting with the board, which usually lasts a few hours. So you just do as you were supposedly told and play right into the hands of a cybercriminal.
A lot of internal company information is actually not a secret but comprehensible to the outside, including cybercriminals who do their homework properly and even scan private social media accounts.
TIP: Be stingy when it comes to information disclosure (over private or official accounts). If possible, don’t implement out-of-office replies for senior executives but rather have those messages relayed internally to a representative in charge.
Busted #3 (Aka: 12345 should work)
You read about its importance over and over again, while still being amused by the best ranking #fails of the year. In spite of all of this, one quickly falls victim to one’s own comfort and routine when it comes to: good passwords.
Employees just like c-level-management, are often unaware of the dangers that come with a weak password, even for everyday life things like social media accounts. Until it’s too late…
TIP: Change your passwords on a regular basis, and never (ever) send them over e-mail channels. In a corporate environment, a password policy should ensure compliance with cybersecurity basics.
Both companies and private users can benefit from password management tools to keep passwords up-to-date and shareable even when working with distributed teams. You might want to take a look at this article by Emsisoft on how to actually create a sufficiently strong password, so that you can strike the following scenario off your bucket-list:

Busted #4 (Aka: I can’t read this)
You receive a PDF file from a co-worker who seems to have a problem with his computer. The program keeps constantly crashing when opening a certain file, so he comes over to your desk and asks you to help him out.
TIP: Be careful! The document causing the program to crash might be manipulated. Report it to your IT department rather than opening it yourself. Don’t forward it to another person (because your computer may start hanging too) unless you want to help the infection to spread.

Busted #5 (Aka: The bitter-sweet symphony)
In the flood of information that surrounds us every day, cybercriminals often rely on very simple yet effective methods to conceal their bad intentions.
TIP: Be sure to verify the EXACT URL before you follow any link or transfer any data for a payment request, document submission, web page etc. …
Here is a little test: would you have spotted the difference?
Note: these are not criminal sites but just examples of how unobtrusively a web address can be manipulated without raising a red flag.
- You want to go to SEC Consult: secconsult.com (instead of sec-consult.com)
- You want to go to Paypal: päypal.com (instead of paypal.com)
- You want to go to Google: google.swiss (instead of google.ch)
- You want to go to Adidas: adidas.net.au (instead of adidas.net)
- You want to go to McDonalds: mc-donalds.at (instead of mcdonalds.at)
- You want to go to Audi: audi-fahrzeuge.de (instead of audi.de)
Busting The Bad: When All Seems Lost
We want to share a concrete example of what could happen in case of an actual hack. When all other security measures have failed, you can rely on the IT experts at SEC Consult and CyberTrap to be your last line of defense.
Note: names of involved persons and companies have been anonymized, for obvious reasons.
Phase 1: Your "Boss" Has A Special Task For You
It’s 12:40 on a Friday afternoon. Mr. Max Meier, head of the company Mustermann, is at the Management Jourfix meeting like every other Friday and not available. Ms. Helga Huber, accountant of the company Mustermann, receives an email from Mr. Meier, with reference to an upcoming transaction and cooperation with the law office ABC.
From: Mag. Max Meier <m.meier@firma-mustermann.com>
Subject: Order-11337
Return_Path: m.meier@firma-mustermann.com
SendTo: h.huber@firma-mustermann.com
CopyTo: christian.kriminell@kanzlei-abc.de
Dear Ms. Huber,
I’m informing you about a confidential financial transaction that
must be finalized with your help and I have informed Mr. Christian
Kriminell, our partner at the law firm ABC already.
Please contact him immediately by e-mail at
christian.kriminell@kanzlei-abc.de
or call +43 720 123 456 so he can send you the
bank details for the first downpayment of the operation.
Please strictly follow his further instructions.
In your message or call, specify the reference-no. Order-11337.
Please be sure to provide the necessary confidentiality
regarding this dossier as you will be
the only contact between our group and the law firm until
the official announcement, which will take place very soon.
I myself have signed a confidentiality agreement.
All our future communications on this transaction will be
made via Mr. Kriminell’s e-mail address. I count on your
responsiveness as the law firm oversees the development of this dossier, which is particularly
important to me.
Best regards,
Mag. Meier
Ms. Huber has already handled a number of cases with the law firm ABC, which has been representing every case of the company for years. Since Mr. Meier often delegates these activities to her at the last minute and apparently Mr. Kriminell is a new partner in the law firm ABC, she is pleased to be informed in advance this time.
Phase 2: The "Colleague" Answers as Expected
It does not take long before there is an answer from Mr. Kriminell, referring to the mentioned transaction:
Dear Ms. Huber,
Could you call me back about the e-mail?
Best regards,
Christian Kriminell
Senior partner
Law firm ABC
Schottenring 104
A-1010
Vienna
austria
T: +43 7 201 234 56
M: christian.kriminell@kanzlei-abc.de
After a short phone call with Mr. Kriminell (in accent-free English), Ms. Huber is in the picture and does the transaction requested by her boss.
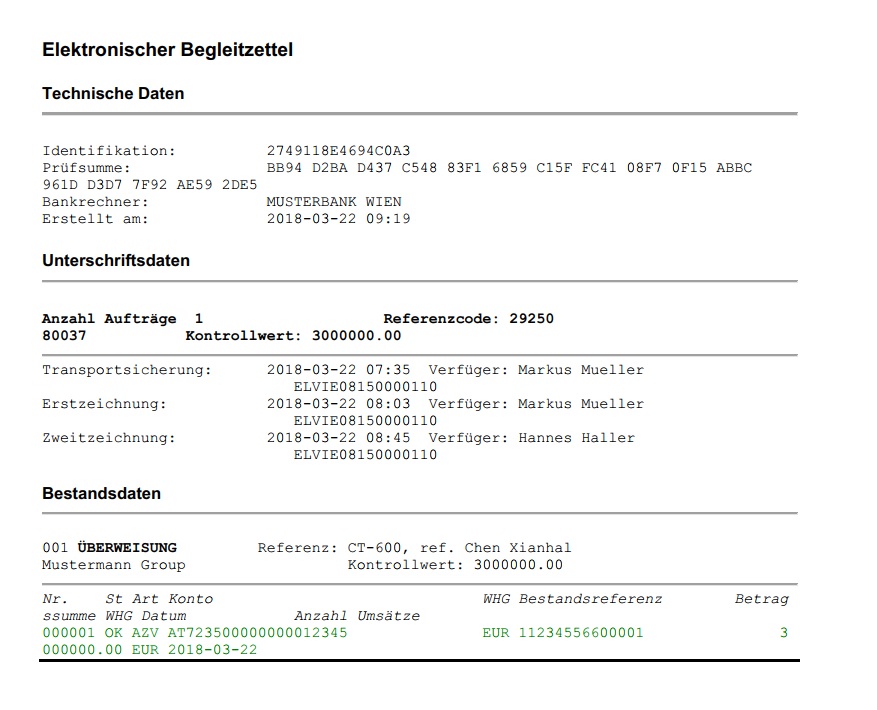
Phase 3: Money Is On Its Way
Surprisingly, Mr. Mustermann calls Ms. Huber to change his hotel booking for the weekend, at this very instant. A lucky concidence, because no one would have noticed the fraud until his return three weeks later and Mr. Kriminell would abscond with the money.
Now it’s time to act quickly. The transfer is cancelled just in time and Mr. Mustermann turns to the SEC Defence Team, who set up a meeting with the specialists of CyberTrap. In order to not raise the criminal’s suspicion, they simulate a transfer by faking appropriate transfer vouchers. The transaction documents are equipped with virtual tracking devices (“TrackDown documents”). Ms. Huber sends a short message to Mr. Kriminell.
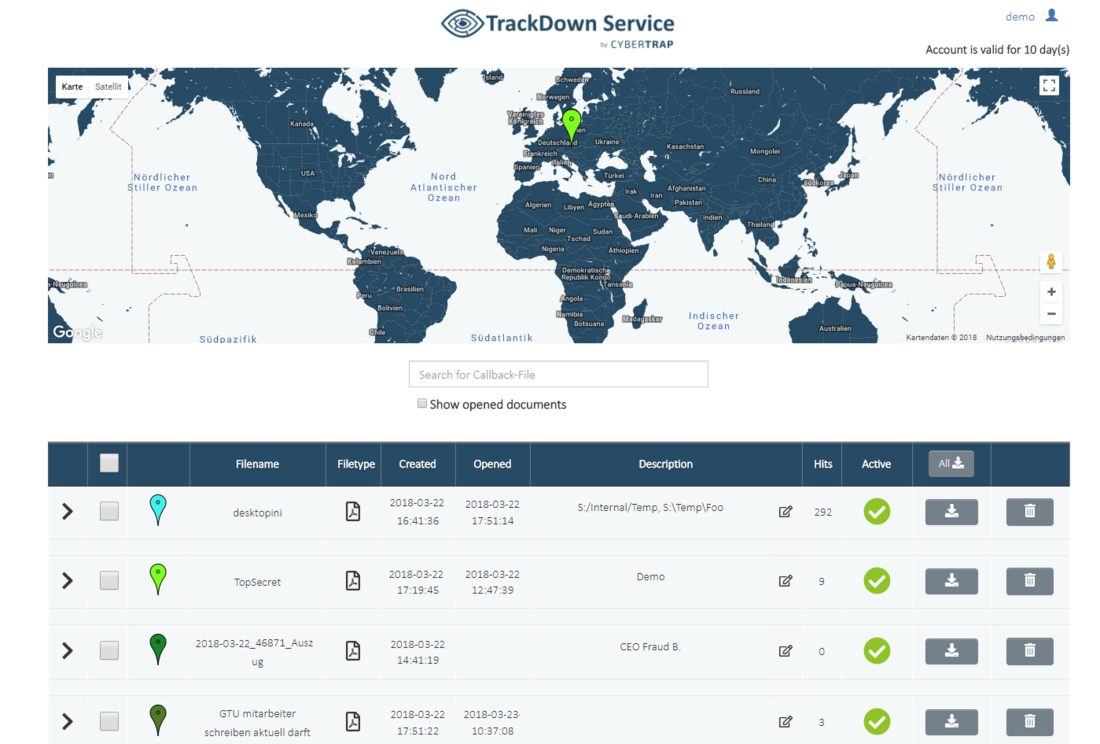
Phase 4: The Money Is (Usually) Gone
Every opening of the document will be registered and important information to prosecute the fraudster will be transmitted back to CyberTrap.[1]
Only 20 minutes go by and Mr. Kriminell opens the manipulated document in Dubai.
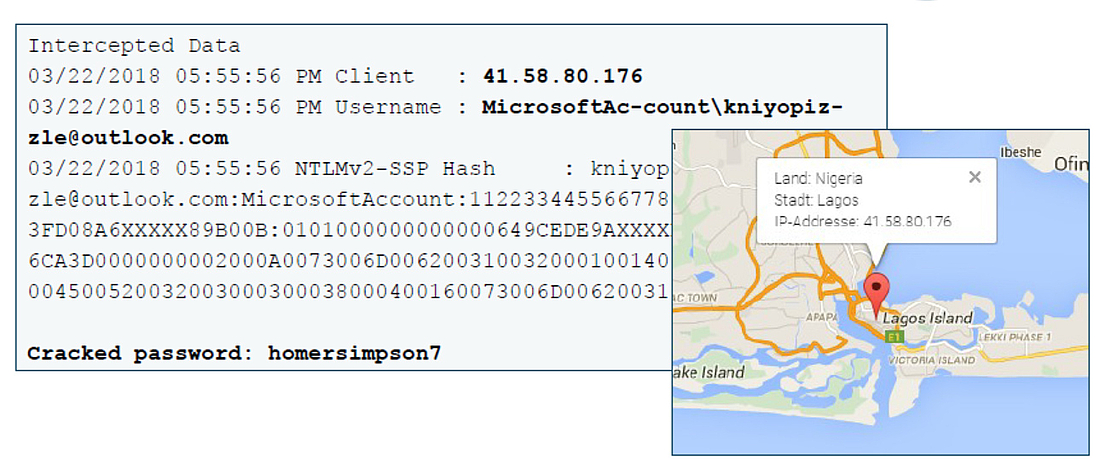
Luckily, the document was forwarded to an additional person. By opening the trackdown documents, his identity and hiding spot in Nigeria were also revealed.
An End Without Fear
Ultimately, not only Mr. Kriminell but also his accomplice could be arrested by legal authorities, and damages of around 245,000 euros are averted. For a fraction of this amount, the company Mustermann is now a grateful customer. The track-down method used is just one of our proven deception technology tools.
If all else fails, CyberTrap can be the last – or the first – line of defense for your business. You need to rule out that an attacker may be already sitting within the system and is just waiting for a favorable moment to gain clarity about your security status. Only if you know whether and, above all, who is trying to penetrate your system, can you act in time and prevent substantial damage.
One thing is for sure, though: There will always be another attack.
3-Step Security: SEC Defence Services
Be prepared for the worst case
Advanced persistent threats cannot be kept away from the internal network by firewalls, virus scanners, or encryption. The
prepares you for a potential crisis, inspects the actual situation of your company, and recommends individual defense measures.Alert in case of emergency
If an attacker has been detected by an early warning system such as CyberTrap or directly by you, contact our SEC Defence Emergency Number immediately.
Damage control and lessons learned
Our SEC Defense Rapid Response Squad (RRS) is ready for action throughout Europe. Experts in the areas of forensics, reverse engineering, as well as technical and organizational information handle system hotfixes, analyze malware, generate antivirus feeds, close backdoors, and prevent further attacks.

