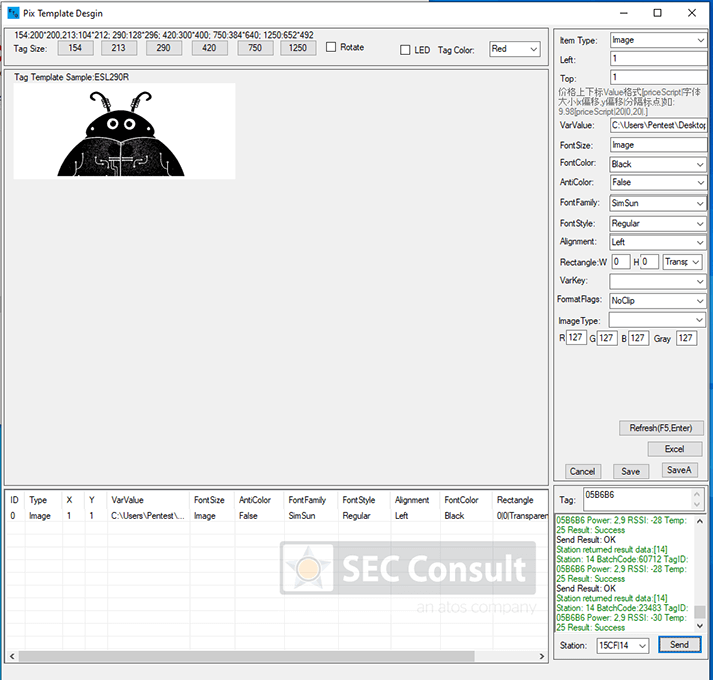
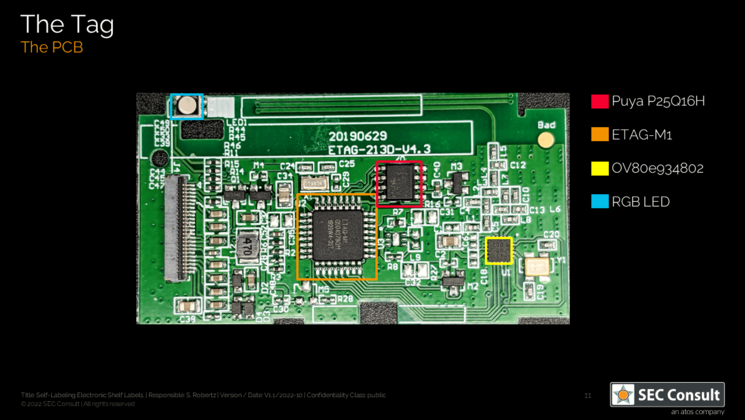
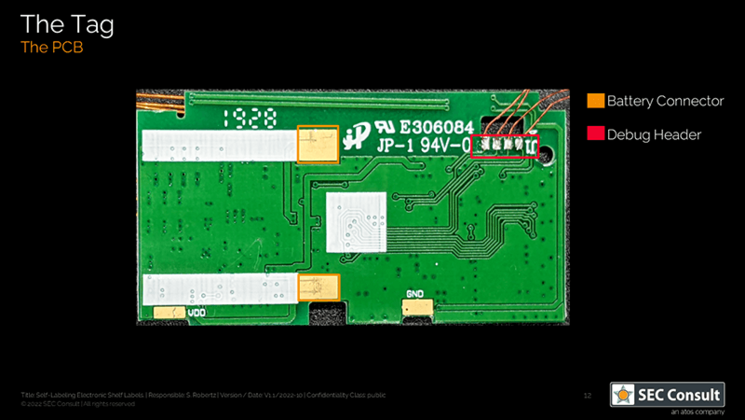
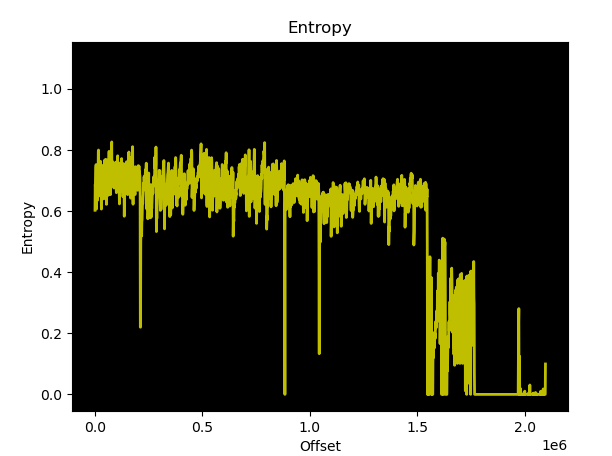
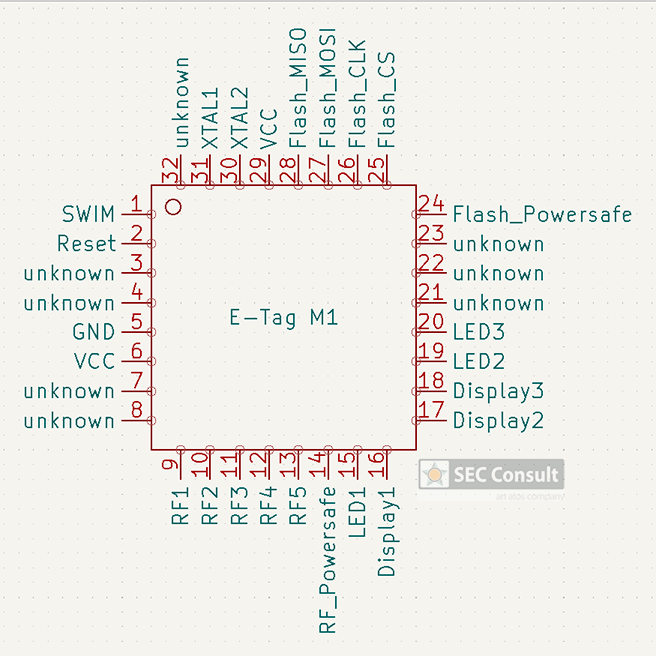
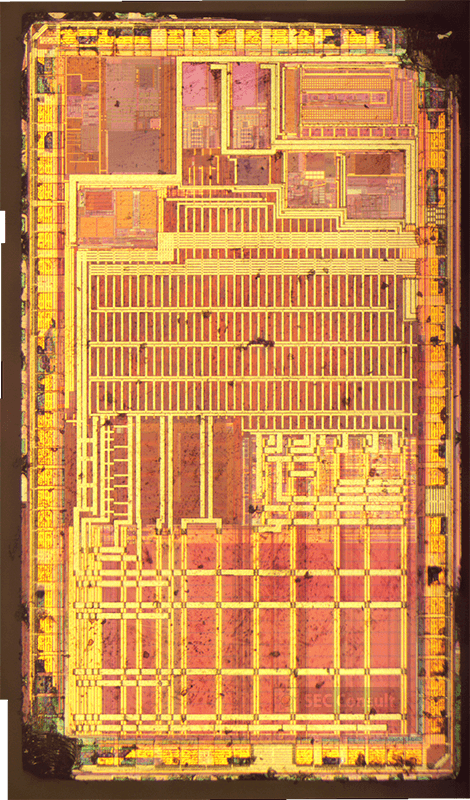
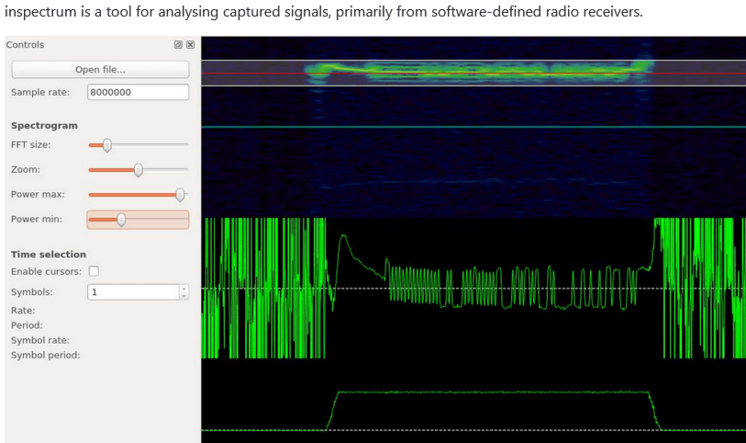
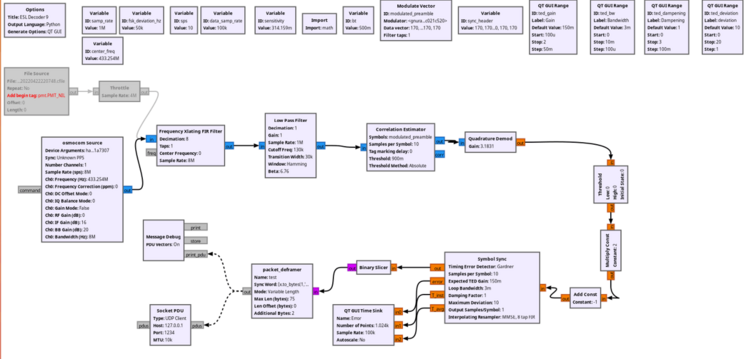
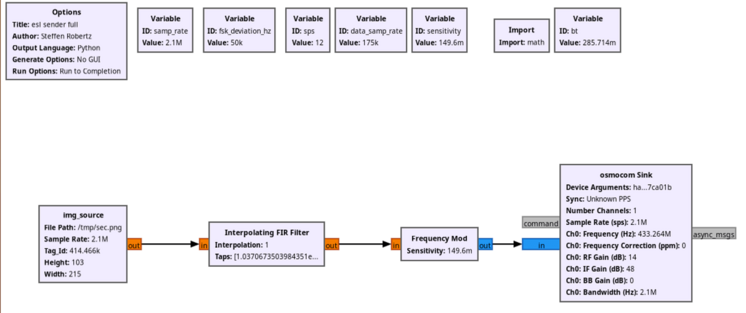
Other use cases include hospital storage for medical equipment or drugs, room labels, or organizing court documents in archives. During our research, we analyzed the unknown micro-controller (MCU) of the SUNY ESL tag, which is a common Chinese ESL tag vendor, gained debug access and reverse engineered the proprietary 433 MHz radio-frequency (RF) protocol. As no authentication is used, we were able to update any ESL tag within RF range with arbitrary content. This research was performed in the SEC Consult Vulnerability Lab by our hardware security expert Steffen Robertz and has been presented by him at multiple conferences, including Hardwear.io USA 2022, Australian Cybersecurity Conference 2022 and BSides Vienna 2022. Additionally, the talk will be presented at this year’s Thotcon conference in the US.
Introduction
ESL is an abbreviation for "electronic shelf label". An ESL tag usually consists of an E-Ink display, a battery and some form of wireless transceiver (e.g., Bluetooth LE or proprietary RF protocols). These tags are deemed to be the next big thing in retail as they offer convenient price changes and can interact with customers by flashing lights and drawing the customers' attention to specific products. Multiple business studies back up this claim by projecting a market growth of over 600% within the next 10 years.