A few weeks after our publication, Zyxel firewalls and VPNs made the news with another critical issue discovered by Jacob Baines, lead security researcher at Rapid7. Given the impact of the vulnerability and amount of exploitation attempts on businesses worldwide, people didn’t seem to care a lot about the „small“ buffer overflow situation found by Gerhard Hechenberger, Steffen Robertz, Thomas Weber and Stefan Viehböck.
What was it all about?
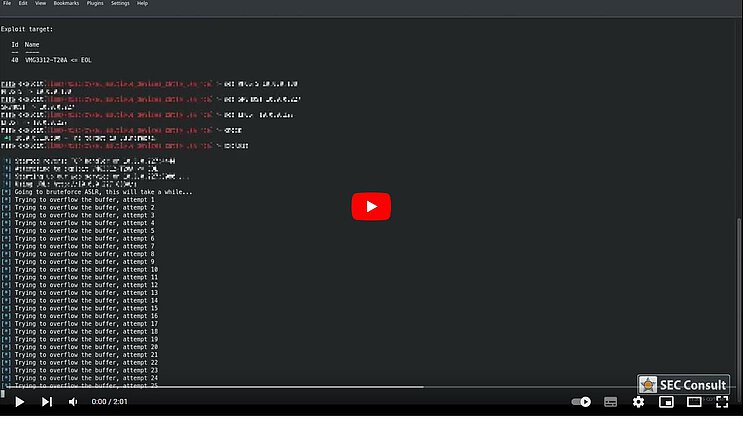
By bypassing the ASLR security measure, our identified buffer overflow can be turned into an unauthenticated remote code execution on the affected Zyxel devices resulting in root permissions for the attacker. And the only prerequisite: network-level access to the web interface, e.g., via your Wi-Fi network but also via the Internet.
Upon responsible disclosure of the advisory in February 2022, we did remove the detailed proof of concept to give ISPs and end users worldwide more time to patch their affected devices. And there were a lot of them. With a few lines of code, an attacker could install backdoors on your router device, reroute traffic (a fun one, right?), sniff out other (maybe harder to crack) passwords for your online banking, social media accounts and basically any other data that is being sent in and out the network. And don't even get us started what you can do in case your router’s web interface is accessible from the Internet…
What is the difference between the vulnerability published in May and our „smaller“ one from February?
Actually, we do have a very similar effect here. The main difference is that the affected devices on our list are mostly used as CPE (customer premises equipment) devices at Internet Service Providers for individuals or small businesses and the firewalls being under attack in May were mainly used by larger companies. Also, more firewalls could be found and accessed over the Internet in comparison to the CPE devices. See the full list of affected devices provided by the vendor further down below.
Why are you telling me this, now?
Everyone is so keen on improving cyber security in your network. But it only takes one device in your own four walls to open up a huge security gap. And it is not always your garage door or the fancy IoT web cam (e.g. the issues we found in HiKam that also got nominated for the Pwnie awards 2022). On that note, we recommend reading up on our top ten vulnerabilities here, which don‘t seem to ever get old here.
Remember the „few lines of code“ you’d need? Well, we just released our Metasploit module for the buffer overflow for Zyxel’s web server on Github. So, with the click of a button, you can test if your own device is already patched instead of waiting for a hacker to do all the fun things mentioned earlier.
We’d really like you to check the list of affected products, some of which remain unpatched because they were considered end-of-life products (EOLs) by Zyxel. But a lot of products are used by not tech-savvy (so called „normal“) people worldwide, regardless of their product lifecycle. It can only be assumed how many of them will not be replaced by a newer (patched) model or get a manual update, thus remain most likely vulnerable.
If you happen to have a friend owning a coffee shop (or any other place with public Wi-Fi), you can invite them to run our provided Metasploit code there too and let them know that they urgently need to patch their routers. For your Wi-Fi security at home, making sure your passwords are strong and updated on a regular basis is a solid recommendation you should always keep in mind.
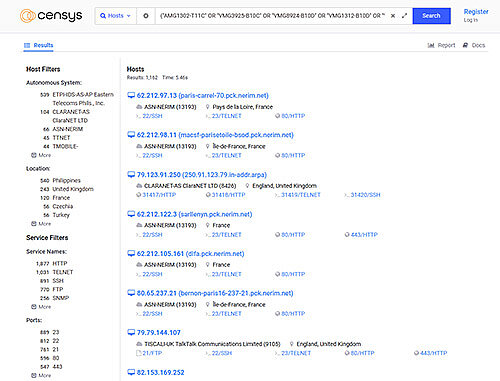
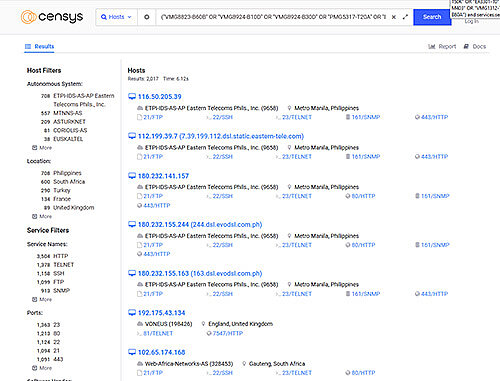
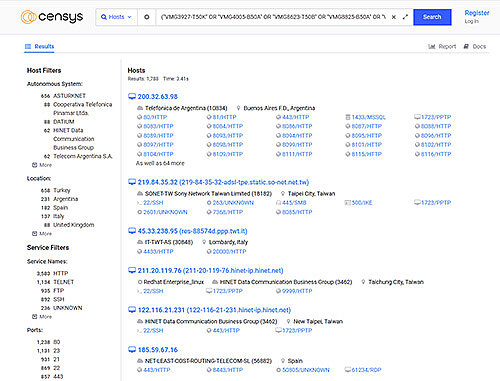
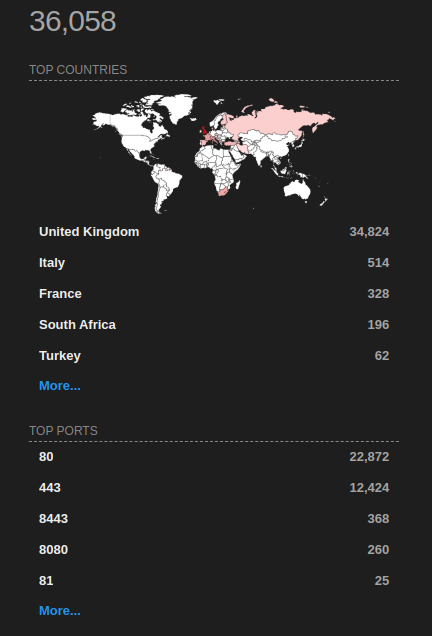
In a recent Censys.io scan for potentially vulnerable Zyxel products, we found over 5000 devices that seem to be accessible over the Internet. The affected numbers for locally exploitable devices are unknown to us.
How many users are still affected?
By searching for the affected device name string one can also filter for HTTP services. Most found devices have the Zyxel web interface exposed (besides other internal ports forwarded) and it seems the number of accessible devices is at least over 5000. This does not necessarily mean that they are all unpatched. But it is never a good idea to expose those admin interfaces directly on the Internet. Those queries and filters have been used which had to be split up because of the amount of devices: