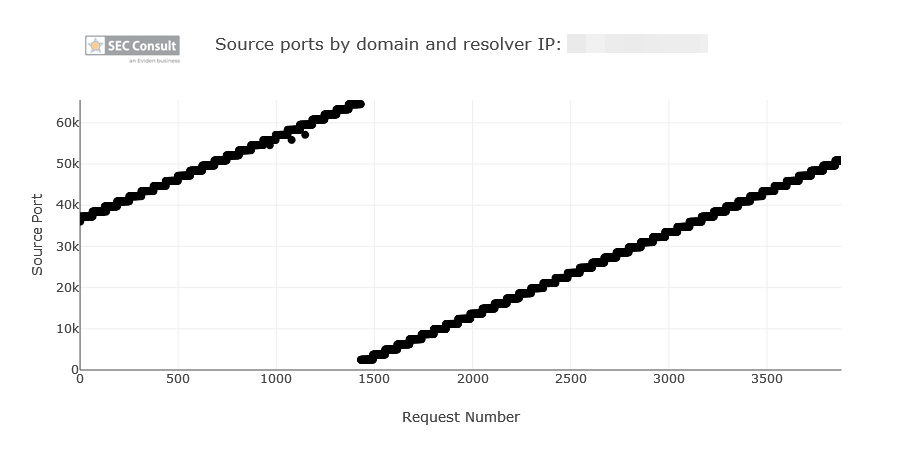
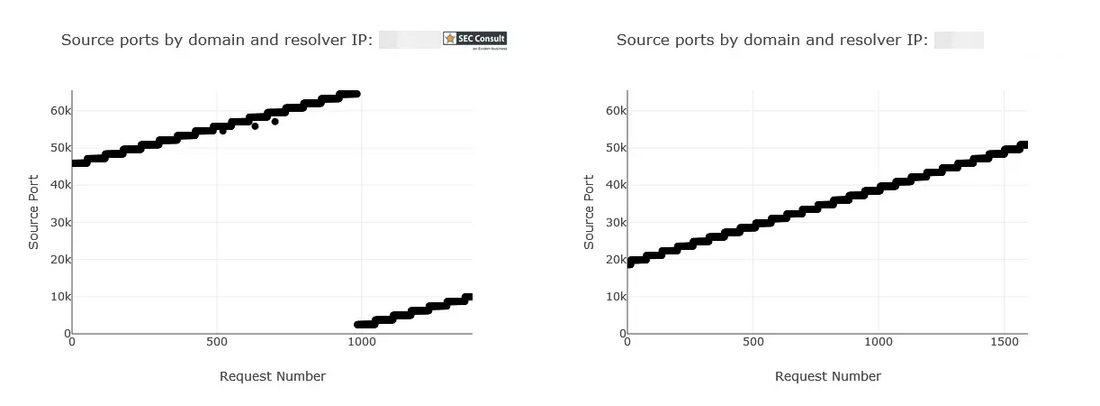
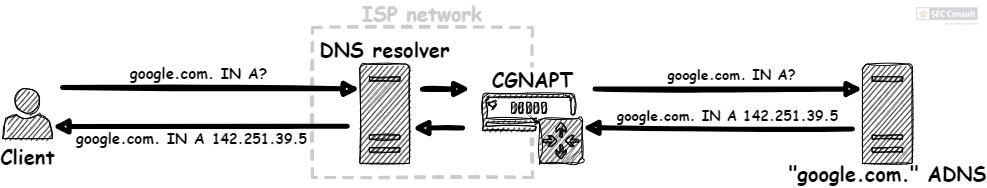
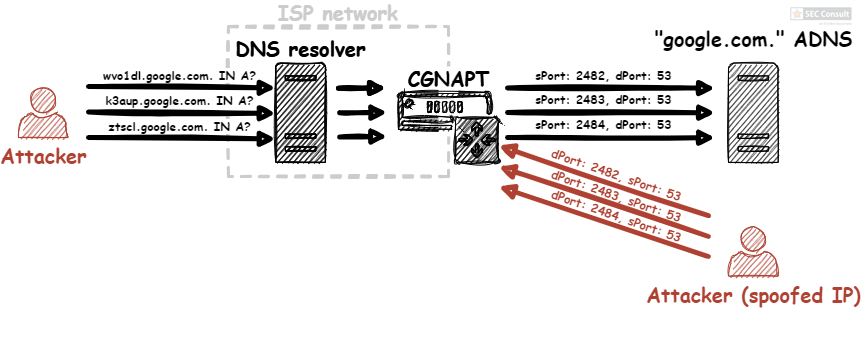
- The attacker sends a DNS request for an A record of a random subdomain of “test1234.demo-admin.ga” (e.g., “sf5ldi.test1234.demo-admin.ga”) to the DNS resolver.
- Since the random subdomain “sf5ldi.test1234.demo-admin.ga” is not yet cached in the resolver, it sends a DNS request to the ADNS of “demo-admin.ga”.
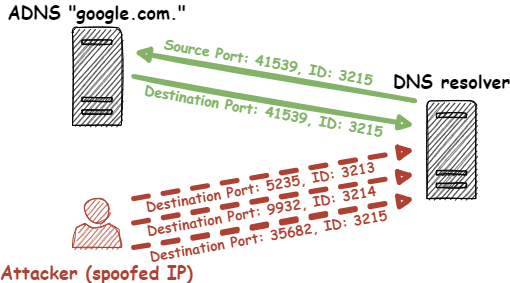
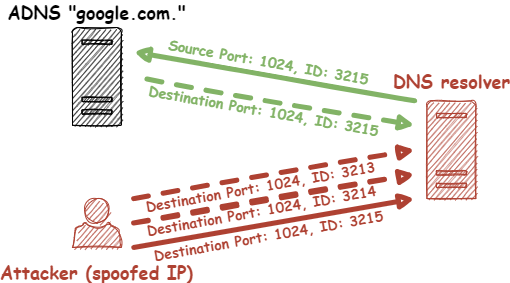
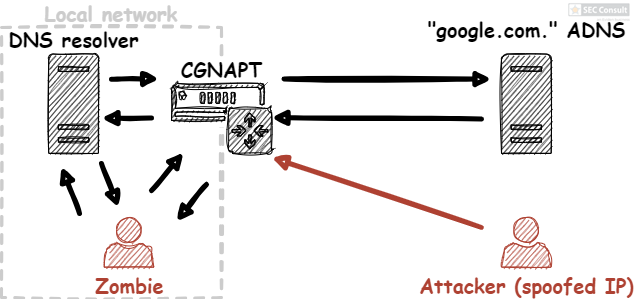
- The CGNAPT device receives the DNS request and overwrites the UDP source port with one of the first 10 possible incremental source ports.
- The “demo-admin.ga” ADNS receives the request and returns a DNS response. While this is happening, the attacker continuously sends a barrage of malicious DNS responses with varying DNS IDs on the 10 possible ports with the source IP address of the “demo-admin.ga” ADNS. The DNS response contains the following entry in the NS section:
test1234.demo-admin.ga IN NS ns1.demo-attacker.ga
- The DNS resolver receives a malicious DNS response of the attacker with the correct port and DNS ID, before it receives the legitimate response. The DNS resolver caches the malicious entry returned by the attacker.
- The DNS resolver returns the manipulated response.
If this procedure fails to poison the “test1234.demo-admin.ga” subdomain in the first run, we can repeat it indefinitely by incrementing the source-port guess by 1.
After we manage to point “test1234.demo-admin.ga” to the attacker ADNS “ns1.demo-attacker.ga”, every DNS request for “test1234.demo-admin.ga” or a subdomain of it gets delegated to the attacker nameserver. The “dig” command can be used to confirm that the cache poisoning worked.
$ dig @RESOLVER_IP test1234.demo-admin.ga
; <<>> DiG 9.16.15-Debian <<>> @RESOLVER_IP test1234.demo-admin.ga
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 43612
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;test1234.demo-admin.ga. IN A
;; ANSWER SECTION:
test1234.demo-admin.ga. 86400 IN A 1.2.3.4
;; Query time: 320 msec
;; SERVER: RESOLVER_IP#53(RESOLVER_IP)
;; WHEN: Tue Jan 17 12:58:34 EST 2023
;; MSG SIZE rcvd: 67
The Impact
After all that, what can we actually do?
Denial of Service (DoS): At the very least, we can bend DNS resolutions to invalid targets. Want to access www.google.com? Too bad, it's now pointing to 127.0.0.1.
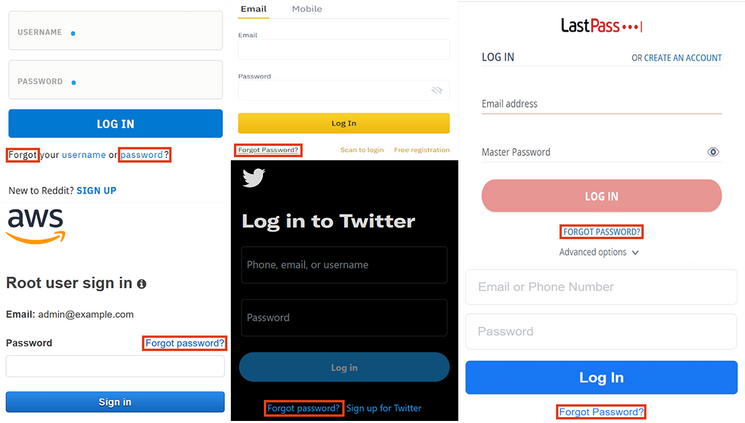
Traffic redirection: Redirecting traffic to an attacker server can be more or less effective depending on the context. Nowadays, with lots of services using and enforcing TLS, Man-in-the-Middle (MitM) attacks may not allow a lot of room to play with. This is especially the case for web applications. However, other fields like e-mailing are not as advanced in terms of TLS and certificate verification. As shown in our previous blog post "Forgot password? Taking over user accounts Kaminsky style", this allows us to redirect e-mails to our attacker server.
E-mail spoofing: SPF, DKIM and DMARC are mechanisms for e-mail authenticity that are all based on DNS. Therefore, manipulating the DNS resolution of a receiving e-mail server allows us to spoof arbitrary sender domains.
Bypassing domain verification: Certificate authorities (CAs) sometimes fully rely on DNS to verify the ownership of a domain. Manipulating the DNS resolution of a CA potentially allows us to issue certificates for arbitrary domains. This was also shown in "Domain Validation++ For MitM-Resilient PKI" by Markus Brandt et al. in 2018.
However, this only scratches the surfaces. More DNS-based attacks might be possible depending on the context.
Bottom line: You don't want a country-wide DNS fallout!
Conclusion
Even 15 years after Dan Kaminsky revealed the Kaminsky attack, DNS is still a critical and sometimes vulnerable part of Internet infrastructure. From time to time security researchers demonstrate the inherent issues carried by this ancient protocol. With our "TRAP; RESET; POISON" attack, we again shed light on one of the many aspects that must be considered when securing the DNS protocol. Even though attacks on (CG)NAPT devices in combination with DNS are known since 2012, we assume that many more DNS setups are affected. The challenge of identifying (CG)NAPT devices suggests that what we've seen might only scratch the surface. But this is research for another day!
This concludes the third installment of the "Kaminsky style" series. In the next part, we may even poison the entire planet!
This research was done by Timo Longin and published on behalf of the SEC Consult Vulnerability Lab.