Vendor Description
“From the start, the Fortinet vision has been to deliver broad, truly integrated, high-performance security across the IT infrastructure. We provide top-rated network and content security, as well as secure access products that share intelligence and work together to form a cooperative fabric. Our unique security fabric combines Security Processors, an intuitive operating system, and applied threat intelligence to give you proven security, exceptional performance, and better visibility and control–while providing easier administration.”
Source: https://www.fortinet.com/corporate/about-us/about-us.html
Vulnerability Overview / Description
The FortiGate SSL VPN Portal is prone to a reflected cross-site scripting (XSS) vulnerability. The HTTP GET parameter “redir” is vulnerable. An attacker can exploit this vulnerability by tricking a victim to visit a URL. The attacker is able to hijack the session of the attacked user, and use this vulnerability in the course of spear-phishing attacks, e.g. by displaying a login prompt that sends credentials of victim back to the attacker.
Note: This vulnerability is also an open redirect and is very similar to a vulnerability that was fixed in FortiOS in March 2016 (FG-IR-16-004).
https://www.fortiguard.com/psirt/fortios-open-redirect-vulnerability
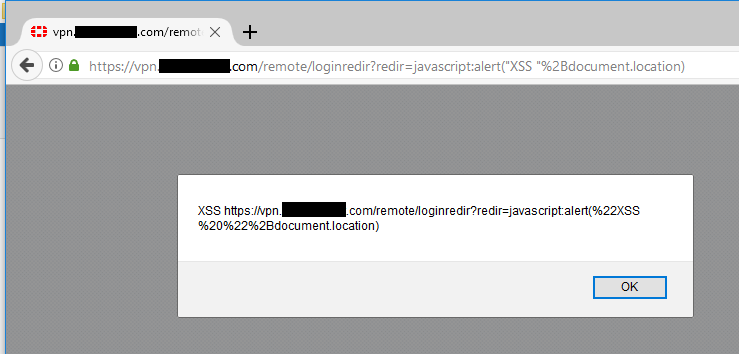
Proof Of Concept
The following request exploits the issue:
vpn..com/remote/loginredir?
redir=javascript:alert(%22XSS%20%22%2Bdocument.location)