Here are the top 10 vulnerabilities unearthed by the SEC Consult Vulnerability Lab in 2023, contributing to ongoing efforts to safeguard digital environments.
About smugglers, bumblebees and dinosaurs - and how to take over the world
news

Bypassing Android biometric authentication
They are always and everywhere: smartphones and co. The Android mobile operating system uses biometric authentication via FingerprintManager API (in older versions) or BiometricPrompt API (since Android 9) to protect data locally. Using a Frida script, a Vulnerability Lab expert hooked into the authenticate method of the BiometricPrompt API to detect an authentication attempt. Within the hook, the script then makes a callback to onAuthenticationSucceeded to trigger a successful authentication. This works if 1. the app does not rely on cryptography, 2. the app uses inappropriate settings for the key, and 3. the protected data is not critical to the authentication process. Although the hurdles for a potential attacker are quite high, as he must have root rights on the victim's device or persuade the victim to install a modified version of an app with unauthorized biometric authentication and have physical access to the device, more care would be desirable on the part of the manufacturers.
Researcher: Leonard Eschenbaum
Multiple security vulnerabilities in m-privacy TightGate-Pro
TightGate-Pro is a remote-controlled browser system (ReCoBS) that runs on a remote server that can be accessed via VNC rather than on the user's own devices. This is intended to prevent the user's host device from being attacked. SEC Consult experts discovered several vulnerabilities in the server that allow attackers to view other users' VNC sessions, infect the VNC session with keyloggers and launch internal phishing attacks. In addition, a TightGate Pro administrator can push malicious PDFs to the user endpoint. The update web servers, which are only accessible via an SSH tunnel, are also very outdated, dating back to 2003. The problem can be solved by installing "Prestable" packages or mprivacy-tools_2.0.406g, tightgatevnc_4.1.2~1 and rsbac-policy-tgpro_2.0.159, if they are available as hotfixes.
Researchers: Daniel Hirschberger, Steven Kurka, Marco Schillinger
Theft on call "thanks" to modern telephone fraud
Last year, the Vulnerability Lab also evaluated a mobile banking application that offers the possibility of using telebanking functions via phone calls. In the accompanying blog post, the researchers describe how they investigated the threats associated with implicit intents, focusing on a specific scenario where a malicious app intercepts sensitive data transmitted via DTMF signals during a phone call. This vulnerability allows fraudsters to inconspicuously carry out money transactions of up to €5,000 in the name of other users. In addition to the financial damage, there is also the risk of identity theft through an attack via this vector.
Researcher: Fabian Densborn and Leonard Eschenbaum
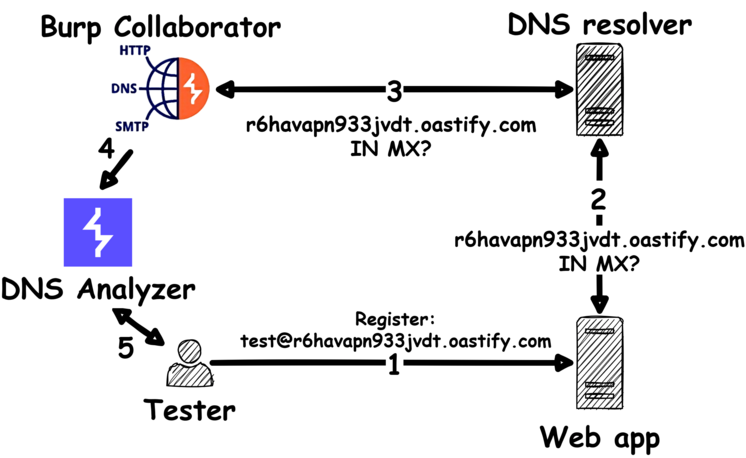
DNS Analyzer - Detecting DNS vulnerabilities with Burp Suite
The SEC Consult team uses the extension of the Burp Suite pentest application to analyze DNS vulnerabilities in web applications. Our security expert Timo Longin had already developed the DNS Analysis Server, which enables fine-grained DNS analysis: a great tool, but one that requires you to set up your own domain, server, etc. The new Burp Suite extension for detecting DNS vulnerabilities in web applications is slimmer - there are detailed instructions on how best to do this in the blog post. Even though bug bounty hunting is now easier, a DNS vulnerability should only be reported if the infrastructure falls within the scope of the bug bounty program and the problematic location has been confirmed by an in-depth DNS analysis.
Researcher: Timo Longin
Let's hunt a BumbleBee: Bumblebee hunt with a velociraptor
An expert from the SEC Defense team analyzed BumbleBee, a malware that is mainly abused by cybercriminals for data exfiltration and is known for ransomware incidents. It is usually distributed via malicious ISO images and uses thread-hijacking emails to trick victims into downloading and then opening the ISO file. To do this, our researcher used detection methods that can help identify an infection in its early stages and thus prevent further malicious activity originating from BumbleBee. They are based on open source tools (e.g. Velociraptor) and rules (e.g. Yara, Sigma) and can therefore be used by any company or the general public. As BumbleBee is closely related to other malware families such as Emotet or IcedID and ransomware groups, a proactive search for BumbleBee activity is useful to detect other malicious executables.
Researcher: Angelo Violetti
Argument injection vulnerability in several Atos Unify OpenScape products
Unify, the collaboration tool from Atos, was the subject of another critical look by a colleague from the Vulnerability Lab. He discovered a critical argument injection vulnerability in the administrative web interface of the Atos Unify OpenScape products "Session Border Controller", "Branch" and "BCF". By manipulating the input parameters, an unauthenticated attacker can gain root access to the application via SSH, bypass the authentication in the administrative interface and gain access as an arbitrary (administrative) user. The vendor provided a patch for the affected products, this concerns Atos Unify OpenScape Session Border Controller firmware version V10 >=R3.4.0; Atos Unify OpenScape Branch version V10 >=R3.4.0 and Atos Unify OpenScape BCF version V10 >=V10R10.12.00 and V10R11.05.02.
Researcher: Armin Weihbold
Visual spoofing of signatures in PDFs
An SEC Consult employee proved that the Vulnerability Lab is not just a research center in name only with his bachelor thesis. He dealt with the question of whether it is possible to imitate the behavior and appearance of signed documents by using the interactive possibilities of PDFs. He examined the current implementations of the PDF specification and tested the spoofing of visual signatures with the commonly used applications Adobe Acrobat Reader DC, Foxit Reader and Okular, evaluated on Windows 10. The result: The core of the threat was the way JavaScript was used in Adobe Acrobat Reader DC, which enabled a credible visual signature forgery. The limited support of JavaScript in the other applications made them less vulnerable. The easiest way to detect visual signature spoofing is to view the PDF file with JavaScript disabled in the application settings. If you also want to get a feel for visual signature spoofing, you can find out for yourself with our proof-of-concept spoofing for Adobe Acrobat Reader DC, which is available for download on our blog post.
Researcher: Tobias Friese
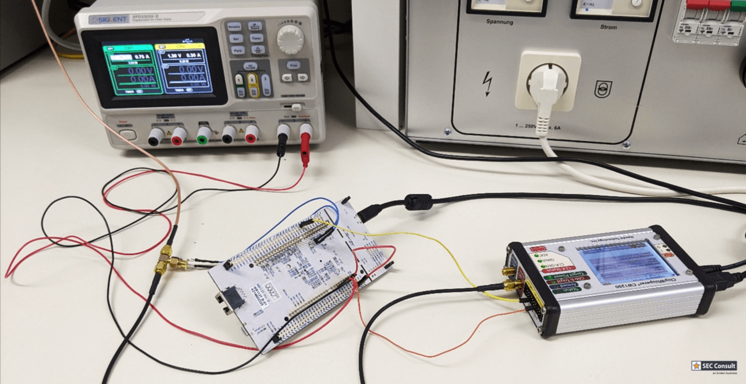
SECGlitcher (Part 1): Reproducible voltage glitching on STM32 microcontrollers
The SEC Consult research department not only deals with software, but also regularly tests hardware in our hardware laboratory. Voltage glitching is a hardware security test that attempts to bypass or alter the normal operation of a device by injecting a fault or a short but precise interruption into the supply voltage. To find out how to make the process more accessible and usable for security assessments, two colleagues turned their attention to the STM32 microcontroller series, which is known for its versatility and affordability and is therefore often used in IoT products. Since emulating glitches can be difficult, mainly due to the use of custom hardware and often unpublished glitching parameters and setups, the team developed the SECGlitcher, which was used to show that the STM32 series must be considered insecure, even when readout protection measures are active.
Researchers: Gerhard Hechenberger and Steffen Robertz
TRAP; RESET; POISON; - how to take over a country Kaminsky-style
An exotic DNS cache poisoning vulnerability was discovered as part of a research project by the SEC Consult Vulnerability Lab, which could have been used to manipulate the DNS name resolution of an entire country. The DNS is still an important and sometimes vulnerable part of the Internet infrastructure 16 years after Dan Kaminsky's discovery of a fundamental vulnerability. Once the attack chain of TRAP; RESET; and POISON; has been completed, cybercriminals have many ways to attack, such as denial of service (DoS), redirecting traffic to an attacker server, email spoofing or bypassing domain scanning.
Researcher: Timo Longin
Siemens A8000 processor module: Multiple vulnerabilities including unauthenticated remote code execution
Vulnerability Lab researchers found that Siemens A8000 CP-8050 and CP-8031 PLCs are affected by a Remote Code Execution (RCE) vulnerability. By sending a crafted HTTP request to Siemens Toolbox II port 80/443, arbitrary commands can be executed without prior authentication. This leads to a complete compromise of the device and may affect its operation. In addition, any user who has access to the SICAM WEB interface can inject system commands that are executed as "root" via the Ethernet Package Capture diagnostic function. A "root" password hash is also permanently programmed into all devices. The vulnerability can be eliminated by updating to firmware CPCI85 V05 or a newer version. The problem can be circumvented by restricting network access to the A8000 CP-8050/CP8031 module or deactivating Toolbox II communication on port 80/443. In addition, physical access to the PLC should be strictly limited during and after its life cycle.
Researchers: Stefan Viehböck, Christian Hager, Steffen Robertz, Gerhard Hechenberger, Gorazd Jank, Constantin Schieber-Knoebl
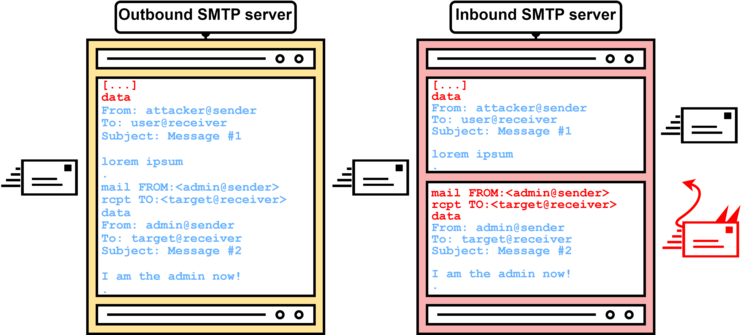
SMTP Smuggling enables global email spoofing
The winner of the year in the SEC Consult Vulnerability Lab's top 10 exploits is clearly the discovery of a novel email spoofing exploit technique that enables targeted phishing attacks. This also earned SEC Consult 3rd place in the PortSwigger Top 10 Web Hacking Techniques of 2023. Differences in the interpretation of the SMTP protocol make it possible to smuggle or send forged emails - hence the name SMTP Smuggling - and still pass SPF matching checks. The problem affects infrastructures of well-known services such as Microsoft Exchange Online and Ionos and means that emails from millions of domains can be smuggled. Although Microsoft and GMX patched this problem immediately, SMTP smuggling to Cisco Secure E-Mail instances is still possible with the standard configurations. You can find out how the standard configurations can be made secure in the blog post.
Researcher: Timo Longin